Command injection targets system commands by exploiting vulnerabilities that allow attackers to execute arbitrary code on the host operating system, often compromising critical device functions. SQL injection manipulates database queries through unsecured input fields, enabling unauthorized data access or modification within pet-related applications. Securing pet technology requires robust input validation and parameterized queries to prevent both command and SQL injection attacks effectively.
Table of Comparison
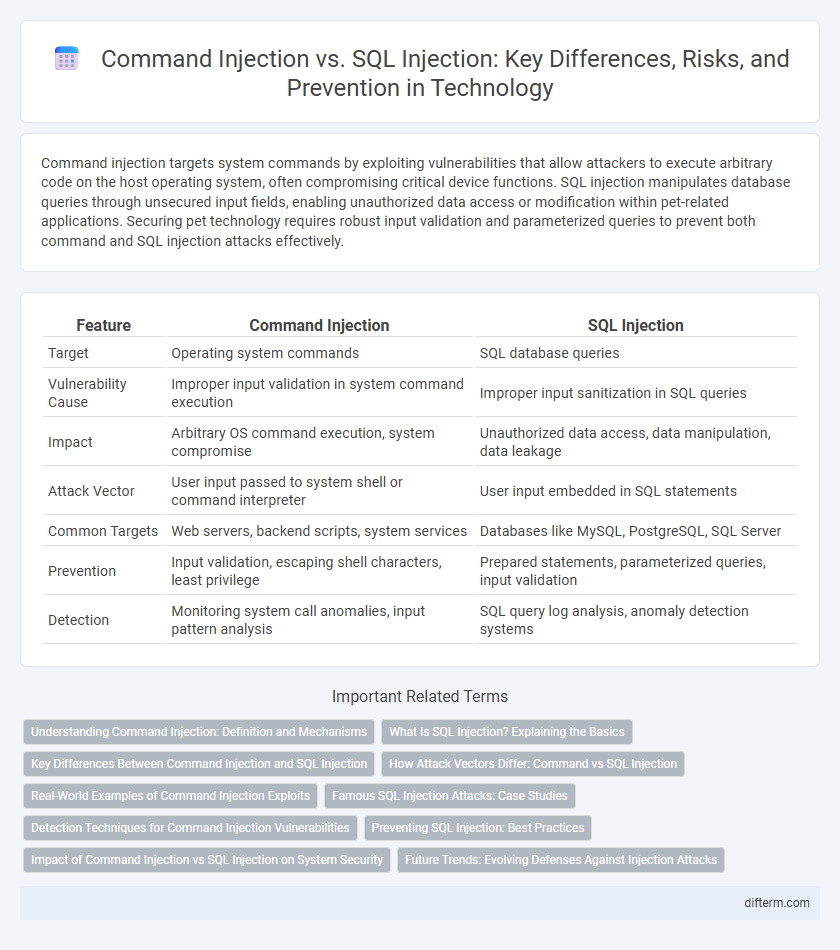
| Feature | Command Injection | SQL Injection |
|---|---|---|
| Target | Operating system commands | SQL database queries |
| Vulnerability Cause | Improper input validation in system command execution | Improper input sanitization in SQL queries |
| Impact | Arbitrary OS command execution, system compromise | Unauthorized data access, data manipulation, data leakage |
| Attack Vector | User input passed to system shell or command interpreter | User input embedded in SQL statements |
| Common Targets | Web servers, backend scripts, system services | Databases like MySQL, PostgreSQL, SQL Server |
| Prevention | Input validation, escaping shell characters, least privilege | Prepared statements, parameterized queries, input validation |
| Detection | Monitoring system call anomalies, input pattern analysis | SQL query log analysis, anomaly detection systems |
Understanding Command Injection: Definition and Mechanisms
Command injection is a critical security vulnerability that allows attackers to execute arbitrary commands on a host operating system via a vulnerable application. It exploits insufficient input validation, enabling malicious input to be passed directly to the system shell, resulting in unauthorized command execution. Unlike SQL injection, which targets database queries, command injection manipulates system-level commands, posing severe risks including data breaches, system compromise, and unauthorized access.
What Is SQL Injection? Explaining the Basics
SQL injection is a cyberattack technique where malicious SQL code is inserted into an input field to manipulate a database and gain unauthorized access or retrieve sensitive data. This vulnerability arises from improper input validation, allowing attackers to alter SQL queries executed by the server. Understanding the fundamentals of SQL injection helps in implementing secure coding practices and safeguarding database-driven applications from such exploits.
Key Differences Between Command Injection and SQL Injection
Command injection exploits vulnerabilities in an application's operating system commands, enabling attackers to execute arbitrary commands on the host server. SQL injection specifically targets database queries, allowing unauthorized access to manipulate or retrieve sensitive data from SQL databases. The primary difference lies in their attack scope: command injection affects the server environment, while SQL injection compromises database integrity and confidentiality.
How Attack Vectors Differ: Command vs SQL Injection
Command injection exploits vulnerabilities by inserting malicious code directly into system shell commands, allowing attackers to execute arbitrary operating system commands. SQL injection targets database query structures by injecting malicious SQL statements into input fields, enabling unauthorized data manipulation or extraction from the database. The attack vector for command injection focuses on operating system-level command execution, while SQL injection targets application-level database query execution.
Real-World Examples of Command Injection Exploits
Real-world examples of command injection exploits include the 2017 Equifax breach, where attackers exploited vulnerable system commands to gain unauthorized access to sensitive data. Another case involved the Jenkins automation server, where improperly sanitized user inputs allowed remote code execution through command injection. These incidents highlight the critical risk of command injection flaws in software systems that fail to properly validate or sanitize input commands.
Famous SQL Injection Attacks: Case Studies
Famous SQL injection attacks, such as the 2017 Equifax breach, exposed sensitive data of over 147 million users due to unpatched vulnerabilities in SQL query handling. The 2018 British Airways hack compromised payment information by exploiting SQL injection flaws in the airline's website infrastructure. These incidents underscore the critical importance of rigorous input validation and parameterized queries to prevent SQL injection attacks, which differ from command injection by targeting databases rather than operating system commands.
Detection Techniques for Command Injection Vulnerabilities
Detection techniques for command injection vulnerabilities primarily involve dynamic analysis methods such as runtime monitoring and taint analysis to trace untrusted input flow within the system. Security tools employ pattern matching and behavioral analysis to identify anomalies indicative of command injection, like unexpected shell command execution or abnormal process spawning. Automated fuzz testing and static code analysis further enhance detection by simulating attack vectors and inspecting source code for insecure command construction practices.
Preventing SQL Injection: Best Practices
Preventing SQL injection requires using parameterized queries and prepared statements, which ensure user input is treated as data rather than executable code. Validating and sanitizing all user inputs further reduces the risk of malicious SQL commands compromising databases. Employing least privilege principles for database access and regularly updating software and frameworks strengthens overall security against SQL injection attacks.
Impact of Command Injection vs SQL Injection on System Security
Command injection poses a severe threat by allowing attackers to execute arbitrary system commands, potentially leading to full system compromise and unauthorized access to critical resources. SQL injection primarily targets database security, enabling attackers to manipulate queries, exfiltrate sensitive data, or corrupt databases, which impacts data integrity and confidentiality. Both vulnerabilities undermine system security but command injection often results in broader system-level consequences compared to the data-focused damage of SQL injection.
Future Trends: Evolving Defenses Against Injection Attacks
Emerging AI-powered security tools demonstrate significant potential in detecting and mitigating command injection and SQL injection attacks by analyzing anomalous patterns in real-time. Advances in machine learning algorithms enhance the precision of intrusion detection systems, enabling faster identification of injection attempts with minimal false positives. The integration of automated patch management and behavior-based anomaly detection is set to become a critical component in next-generation web application firewalls and endpoint security solutions.
Command injection vs SQL injection Infographic
 difterm.com
difterm.com