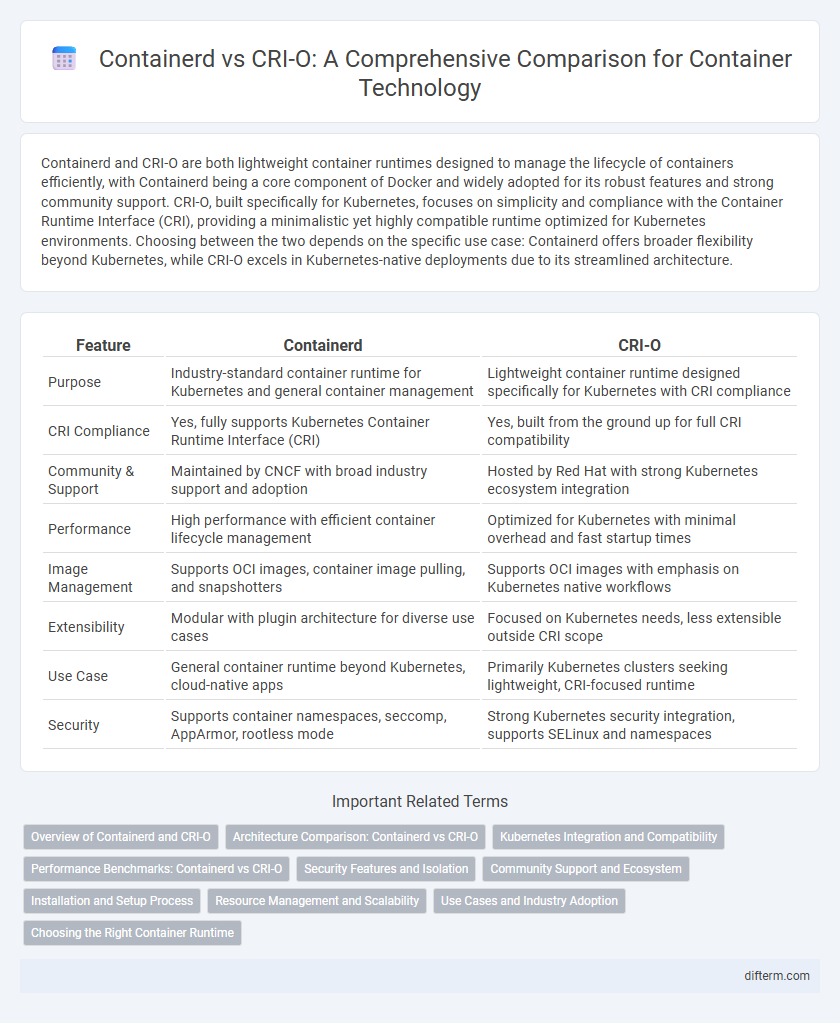
Containerd and CRI-O are both lightweight container runtimes designed to manage the lifecycle of containers efficiently, with Containerd being a core component of Docker and widely adopted for its robust features and strong community support. CRI-O, built specifically for Kubernetes, focuses on simplicity and compliance with the Container Runtime Interface (CRI), providing a minimalistic yet highly compatible runtime optimized for Kubernetes environments. Choosing between the two depends on the specific use case: Containerd offers broader flexibility beyond Kubernetes, while CRI-O excels in Kubernetes-native deployments due to its streamlined architecture.
Table of Comparison
| Feature | Containerd | CRI-O |
|---|---|---|
| Purpose | Industry-standard container runtime for Kubernetes and general container management | Lightweight container runtime designed specifically for Kubernetes with CRI compliance |
| CRI Compliance | Yes, fully supports Kubernetes Container Runtime Interface (CRI) | Yes, built from the ground up for full CRI compatibility |
| Community & Support | Maintained by CNCF with broad industry support and adoption | Hosted by Red Hat with strong Kubernetes ecosystem integration |
| Performance | High performance with efficient container lifecycle management | Optimized for Kubernetes with minimal overhead and fast startup times |
| Image Management | Supports OCI images, container image pulling, and snapshotters | Supports OCI images with emphasis on Kubernetes native workflows |
| Extensibility | Modular with plugin architecture for diverse use cases | Focused on Kubernetes needs, less extensible outside CRI scope |
| Use Case | General container runtime beyond Kubernetes, cloud-native apps | Primarily Kubernetes clusters seeking lightweight, CRI-focused runtime |
| Security | Supports container namespaces, seccomp, AppArmor, rootless mode | Strong Kubernetes security integration, supports SELinux and namespaces |
Overview of Containerd and CRI-O
Containerd is an industry-standard core container runtime designed to provide a minimal, robust, and extensible container execution environment, widely used for managing the complete container lifecycle, including image transfer, storage, and execution. CRI-O is a lightweight Kubernetes container runtime implementation specifically optimized for Kubernetes by directly integrating with the Container Runtime Interface (CRI) to offer a streamlined, secure, and Kubernetes-native container management experience. Both containerd and CRI-O support OCI-compliant images and focus on enhancing container orchestration efficiency within cloud-native infrastructures.
Architecture Comparison: Containerd vs CRI-O
Containerd features a modular architecture built on a daemon with core components handling image management, container lifecycle, and storage, supporting OCI standards for broad compatibility. CRI-O is designed specifically for Kubernetes, implementing the Container Runtime Interface (CRI) with lightweight components optimized for Kubernetes integration and minimal overhead. Containerd offers versatility across environments, while CRI-O's focused architecture delivers streamlined performance tailored to Kubernetes clusters.
Kubernetes Integration and Compatibility
Containerd and CRI-O are both container runtimes designed to integrate seamlessly with Kubernetes, ensuring efficient container lifecycle management and resource optimization. Containerd, originally part of Docker, offers broad compatibility with Kubernetes through the Container Runtime Interface (CRI) and supports OCI (Open Container Initiative) standards, enabling versatile container image handling and runtime operations. CRI-O, built explicitly for Kubernetes, provides a lightweight, Kubernetes-native runtime solution that enhances security and reduces system overhead by strictly adhering to Kubernetes CRI specifications and supporting OCI-compliant runtimes like runc and Kata Containers.
Performance Benchmarks: Containerd vs CRI-O
Containerd and CRI-O both demonstrate efficient container runtime performance, with benchmarks highlighting Containerd's faster startup times and lower CPU overhead. CRI-O excels in memory consumption optimization, particularly in Kubernetes environments, reducing resource usage for large-scale deployments. Benchmark data reveals that Containerd offers better I/O throughput, whereas CRI-O provides improved stability under heavy orchestration workloads.
Security Features and Isolation
Containerd employs robust namespace isolation and seccomp profiles to enhance container security, limiting system call exposure and preventing unauthorized access. CRI-O integrates seamlessly with Kubernetes security modules such as SELinux and AppArmor, providing fine-grained access controls and mandatory access control policies. Both container runtimes support rootless mode, reducing the attack surface by running containers without root privileges.
Community Support and Ecosystem
Containerd benefits from robust community support driven by its integration with Docker and CNCF, resulting in extensive tooling, frequent updates, and widespread adoption across cloud platforms. CRI-O is backed by the Kubernetes community with strong emphasis on lightweight, Kubernetes-native container runtime, fostering a dedicated ecosystem optimized for Kubernetes clusters. Both runtimes maintain active open-source contributions, but Containerd's broader industry adoption offers a more diverse range of integrations and third-party tools.
Installation and Setup Process
Containerd installation involves downloading binaries or using package managers like apt or yum, followed by configuring systemd service files to enable seamless container lifecycle management. CRI-O setup requires adding its official repositories, installing via package managers, and configuring its configuration file to integrate smoothly with Kubernetes as a lightweight container runtime. Both tools emphasize minimal dependencies and easy integration, though CRI-O is optimized for Kubernetes environments, while Containerd provides a more general-purpose container runtime.
Resource Management and Scalability
Containerd excels in resource management by offering lightweight container runtime capabilities that efficiently handle container lifecycle operations, reducing overhead and improving CPU and memory utilization. CRI-O provides robust scalability tailored for Kubernetes environments, integrating seamlessly with the Kubernetes Container Runtime Interface (CRI) to enable streamlined orchestration and enhanced support for large-scale cluster deployments. Both runtimes optimize resource allocation, but CRI-O's Kubernetes-native design offers superior scalability in dynamic, multi-node cluster environments.
Use Cases and Industry Adoption
Containerd excels in cloud-native environments and Kubernetes clusters due to its robust container lifecycle management and wide integration with major cloud providers. CRI-O is favored in enterprises emphasizing lightweight Kubernetes setups and strict adherence to Kubernetes Container Runtime Interface (CRI) standards, ensuring minimal overhead and enhanced security. Both runtimes have significant industry adoption, with Containerd widely embraced by large cloud platforms like AWS and Google Cloud, while CRI-O is prevalent in Red Hat OpenShift and other Kubernetes-centric ecosystems.
Choosing the Right Container Runtime
Choosing the right container runtime depends on factors such as Kubernetes compatibility, performance, and community support. Containerd offers deep integration with Docker and is favored for its stability and extensive plugin ecosystem, while CRI-O, designed exclusively for Kubernetes, provides a lightweight alternative optimized for minimal overhead. Evaluating workload requirements and infrastructure constraints helps determine whether the robust feature set of Containerd or the streamlined efficiency of CRI-O aligns best with your container orchestration goals.
Containerd vs CRI-O Infographic
 difterm.com
difterm.com