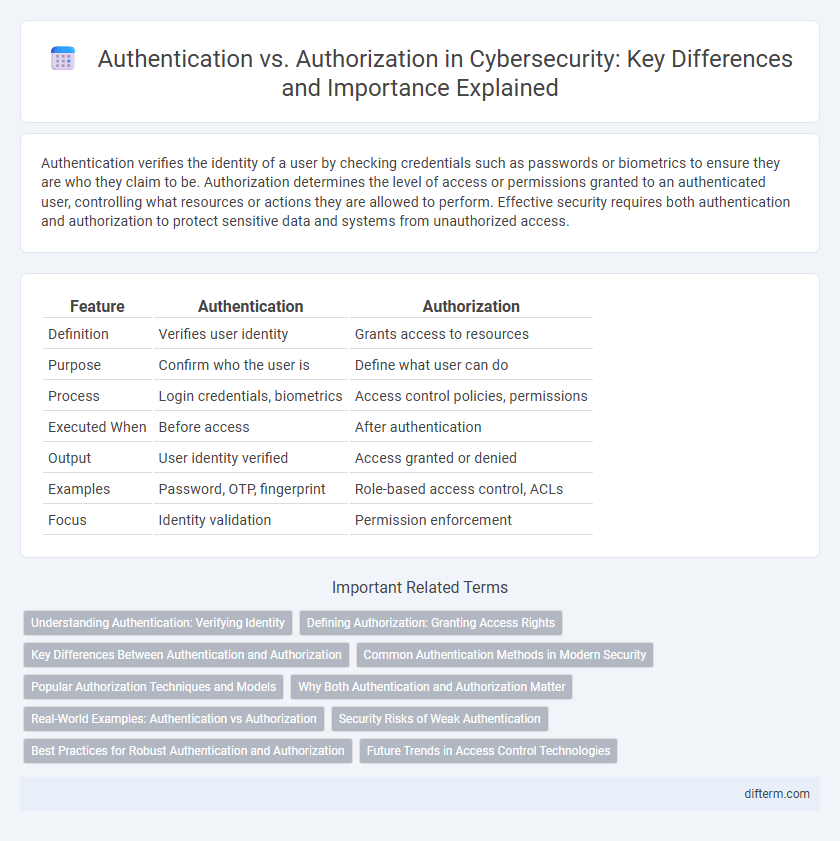
Authentication verifies the identity of a user by checking credentials such as passwords or biometrics to ensure they are who they claim to be. Authorization determines the level of access or permissions granted to an authenticated user, controlling what resources or actions they are allowed to perform. Effective security requires both authentication and authorization to protect sensitive data and systems from unauthorized access.
Table of Comparison
| Feature | Authentication | Authorization |
|---|---|---|
| Definition | Verifies user identity | Grants access to resources |
| Purpose | Confirm who the user is | Define what user can do |
| Process | Login credentials, biometrics | Access control policies, permissions |
| Executed When | Before access | After authentication |
| Output | User identity verified | Access granted or denied |
| Examples | Password, OTP, fingerprint | Role-based access control, ACLs |
| Focus | Identity validation | Permission enforcement |
Understanding Authentication: Verifying Identity
Authentication involves verifying a user's identity through credentials such as passwords, biometrics, or security tokens to ensure access is granted to legitimate users only. It establishes a trusted connection by confirming that the person or system requesting access is who they claim to be, laying the foundation for secure interactions. Robust authentication mechanisms, including multi-factor authentication (MFA), significantly reduce the risk of unauthorized access and identity theft in cybersecurity.
Defining Authorization: Granting Access Rights
Authorization defines the process of granting access rights to users or systems based on predetermined policies and roles, ensuring they can only access resources permitted to them. It operates after authentication verifies identity, enforcing permissions such as read, write, or execute on applications, databases, or network services. Effective authorization mechanisms reduce security risks by preventing unauthorized access and protecting sensitive data.
Key Differences Between Authentication and Authorization
Authentication verifies the identity of a user or system through credentials such as passwords, biometrics, or tokens, ensuring accurate access control. Authorization determines the specific permissions or access levels granted to the authenticated user, controlling what resources or actions they are allowed within a system. These distinct processes operate sequentially, with authentication serving as a prerequisite for authorization in effective security management.
Common Authentication Methods in Modern Security
Common authentication methods in modern security include biometrics, multifactor authentication (MFA), and token-based systems, which enhance the verification process by requiring multiple forms of identity confirmation. Passwords remain widely used but are increasingly supplemented or replaced by more secure methods such as fingerprint scans, facial recognition, and hardware tokens like YubiKeys. These techniques collectively improve identity assurance and protect against unauthorized access in various digital environments.
Popular Authorization Techniques and Models
Popular authorization techniques include role-based access control (RBAC), attribute-based access control (ABAC), and policy-based access control (PBAC), each offering distinct methods for defining user permissions. RBAC assigns access rights based on user roles within an organization, while ABAC leverages user attributes and environmental conditions to enforce dynamic access policies. PBAC utilizes comprehensive policies that incorporate both roles and attributes, enabling granular and flexible control over resource access in complex security environments.
Why Both Authentication and Authorization Matter
Authentication verifies a user's identity by validating credentials such as passwords or biometrics, ensuring only legitimate users gain access. Authorization determines what resources or actions an authenticated user is permitted to use, enforcing access control policies and protecting sensitive data. Both processes are critical in security frameworks to prevent unauthorized access and mitigate risks associated with data breaches and insider threats.
Real-World Examples: Authentication vs Authorization
Authentication verifies identity by confirming credentials such as passwords or biometric data, exemplified when users log into their email accounts using a username and password or fingerprint scan. Authorization determines access levels after identity verification, as seen when a bank employee accesses customer account information only if their role permits it. In cloud services, authentication ensures the user is legitimate, while authorization controls whether they can modify files or simply view them.
Security Risks of Weak Authentication
Weak authentication exposes systems to significant security risks such as unauthorized access, data breaches, and identity theft, compromising sensitive information and critical infrastructure. Attackers often exploit weak authentication mechanisms like simple passwords or lack of multi-factor authentication (MFA) to bypass security controls and escalate privileges. Implementing robust authentication protocols, including MFA and biometric verification, is essential to mitigate these vulnerabilities and protect against sophisticated cyber threats.
Best Practices for Robust Authentication and Authorization
Implementing multi-factor authentication (MFA) significantly strengthens user verification by requiring multiple credentials, reducing the risk of unauthorized access. Role-based access control (RBAC) ensures users receive permissions aligned strictly with their job functions, minimizing privilege escalation risks. Regular audits and real-time monitoring support continuous enforcement of authentication and authorization policies, enabling rapid detection and response to potential security breaches.
Future Trends in Access Control Technologies
Future trends in access control technologies emphasize adaptive authentication methods leveraging AI and biometric advancements to enhance security while maintaining user convenience. Zero-trust architectures will redefine authorization processes by enforcing continuous verification based on real-time context and behavior analytics. Emerging decentralized identity frameworks, such as blockchain-based solutions, promise to revolutionize authentication by providing users greater control over their credentials and reducing reliance on centralized authorities.
Authentication vs Authorization Infographic
 difterm.com
difterm.com