OS credential dumping involves extracting hashed or plaintext credentials directly from a system's memory or storage, enabling attackers to capture sensitive login information. Pass-the-Hash attacks bypass the need for plaintext passwords by reusing captured password hashes to authenticate and gain unauthorized access. Understanding these distinct techniques is crucial for implementing effective security measures and preventing lateral movement within networks.
Table of Comparison
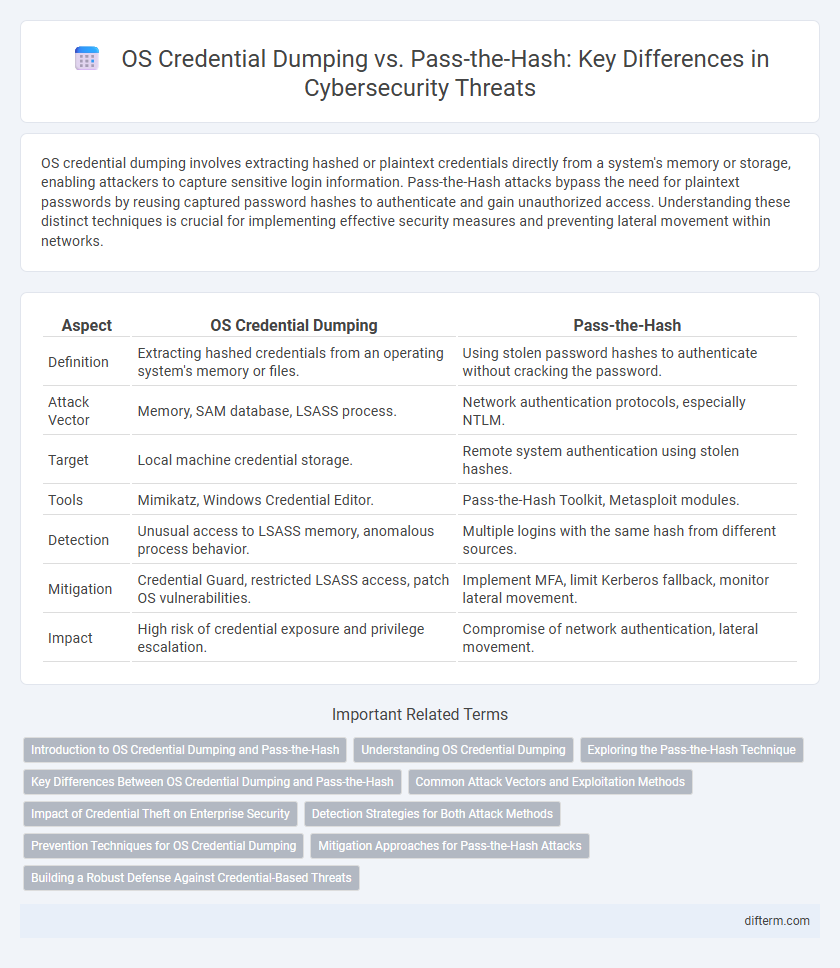
| Aspect | OS Credential Dumping | Pass-the-Hash |
|---|---|---|
| Definition | Extracting hashed credentials from an operating system's memory or files. | Using stolen password hashes to authenticate without cracking the password. |
| Attack Vector | Memory, SAM database, LSASS process. | Network authentication protocols, especially NTLM. |
| Target | Local machine credential storage. | Remote system authentication using stolen hashes. |
| Tools | Mimikatz, Windows Credential Editor. | Pass-the-Hash Toolkit, Metasploit modules. |
| Detection | Unusual access to LSASS memory, anomalous process behavior. | Multiple logins with the same hash from different sources. |
| Mitigation | Credential Guard, restricted LSASS access, patch OS vulnerabilities. | Implement MFA, limit Kerberos fallback, monitor lateral movement. |
| Impact | High risk of credential exposure and privilege escalation. | Compromise of network authentication, lateral movement. |
Introduction to OS Credential Dumping and Pass-the-Hash
OS Credential Dumping involves extracting plaintext passwords, hashes, or Kerberos tickets directly from operating system memory or files, enabling attackers to gain unauthorized access to user credentials. Pass-the-Hash attacks leverage these stolen password hashes to authenticate without cracking them, allowing lateral movement across systems within a network. Understanding the distinctions between these techniques is critical for implementing effective security measures and preventing credential-based attacks.
Understanding OS Credential Dumping
OS Credential Dumping is a technique used by attackers to extract plaintext credentials, hashes, or Kerberos tickets from a compromised system's memory or storage, enabling lateral movement within a network. This method targets tools like Mimikatz or Windows credential storage areas such as the Security Account Manager (SAM) and Local Security Authority Subsystem Service (LSASS). Unlike Pass-the-Hash attacks, which use harvested hashes to authenticate without cracking them, credential dumping involves obtaining raw credentials for broader exploitation.
Exploring the Pass-the-Hash Technique
Pass-the-Hash (PtH) is a cyberattack technique where adversaries capture and reuse password hashes instead of plaintext credentials to authenticate across systems. Unlike OS credential dumping, which extracts actual passwords and hashes stored on the operating system, PtH leverages intercepted hashes to bypass traditional authentication without cracking them. This method exploits vulnerabilities in Windows authentication protocols, enabling lateral movement and persistence within targeted networks without triggering common password-related alerts.
Key Differences Between OS Credential Dumping and Pass-the-Hash
OS Credential Dumping involves extracting plaintext passwords, password hashes, or Kerberos tickets directly from an operating system's memory or storage, enabling attackers to obtain actual user credentials. Pass-the-Hash attacks use stolen password hashes to authenticate without cracking them, allowing lateral movement within networks using hashed credentials instead of plaintext passwords. The key difference lies in OS Credential Dumping being a method to obtain credentials, while Pass-the-Hash leverages those stolen hashes to gain unauthorized access.
Common Attack Vectors and Exploitation Methods
OS credential dumping primarily exploits memory scraping, LSASS process memory, and SAM database extraction to harvest plaintext credentials, while pass-the-hash attacks leverage stolen NTLM hash values to authenticate without password cracking. Common attack vectors include malware, malicious scripts, and exploitation of sysadmin tools like Mimikatz or PowerShell for credential extraction in credential dumping, whereas pass-the-hash utilizes network lateral movement, remote services, and weak authentication protocols. Both techniques exploit improper privilege management and lack of endpoint security controls to escalate privilege and maintain persistence within compromised Windows environments.
Impact of Credential Theft on Enterprise Security
Credential dumping exposes enterprise systems to elevated risks by extracting plaintext passwords and hash values directly from operating system memory. Pass-the-Hash attacks leverage stolen hash credentials to impersonate users without needing to crack passwords, enabling lateral movement within networks. Together, these techniques facilitate unauthorized access, data breaches, and persistent insider threats, significantly undermining enterprise security posture.
Detection Strategies for Both Attack Methods
Effective detection strategies for OS credential dumping involve monitoring unusual access to LSASS memory and auditing privileged processes that extract hash data. Pass-the-Hash attacks require analyzing lateral movement patterns and inspecting network authentication logs for reused NTLM hashes across multiple endpoints. Implementing behavior-based anomaly detection and leveraging endpoint detection and response (EDR) tools enhance identification of both attack methods.
Prevention Techniques for OS Credential Dumping
Implementing Endpoint Detection and Response (EDR) tools enhances real-time monitoring to identify unusual process behaviors indicative of OS credential dumping. Enforcing Least Privilege Access restricts user permissions, minimizing the attack surface for credential theft. Regularly applying security patches and disabling unnecessary Windows services like LSASS memory access significantly reduce vulnerable vectors exploited in credential dumping attacks.
Mitigation Approaches for Pass-the-Hash Attacks
Mitigation approaches for Pass-the-Hash attacks include implementing multifactor authentication (MFA) to reduce reliance on password hashes alone and enforcing least privilege principles to limit lateral movement within a network. Using endpoint detection and response (EDR) tools helps identify suspicious activities related to hash dumping and reuse, while applying Microsoft's Local Administrator Password Solution (LAPS) ensures regularly rotated local account passwords, reducing the risk of credential theft. Network segmentation and disabling NTLM authentication further minimize the attack surface for Pass-the-Hash exploitation.
Building a Robust Defense Against Credential-Based Threats
OS credential dumping involves extracting hashed or plaintext credentials directly from operating system memory or files, enabling attackers to escalate privileges or move laterally within networks. Pass-the-Hash (PtH) attacks exploit these harvested NTLM hash values to authenticate without cracking passwords, posing significant risks in Windows-based environments. Building a robust defense against these credential-based threats requires implementing multi-factor authentication, restricting administrative privileges, deploying endpoint detection and response (EDR) solutions, and continuously monitoring for suspicious logon behaviors.
OS Credential Dumping vs Pass-the-Hash Infographic
 difterm.com
difterm.com