SQL injection targets relational databases by exploiting vulnerabilities in structured query language queries to manipulate or access unauthorized data, often leading to severe breaches. NoSQL injection attacks focus on non-relational databases, utilizing different injection techniques due to the flexible schema and query formats, such as JSON or BSON. Both exploit weaknesses in input validation but require distinct mitigation strategies tailored to the database type to ensure security in pet technology applications.
Table of Comparison
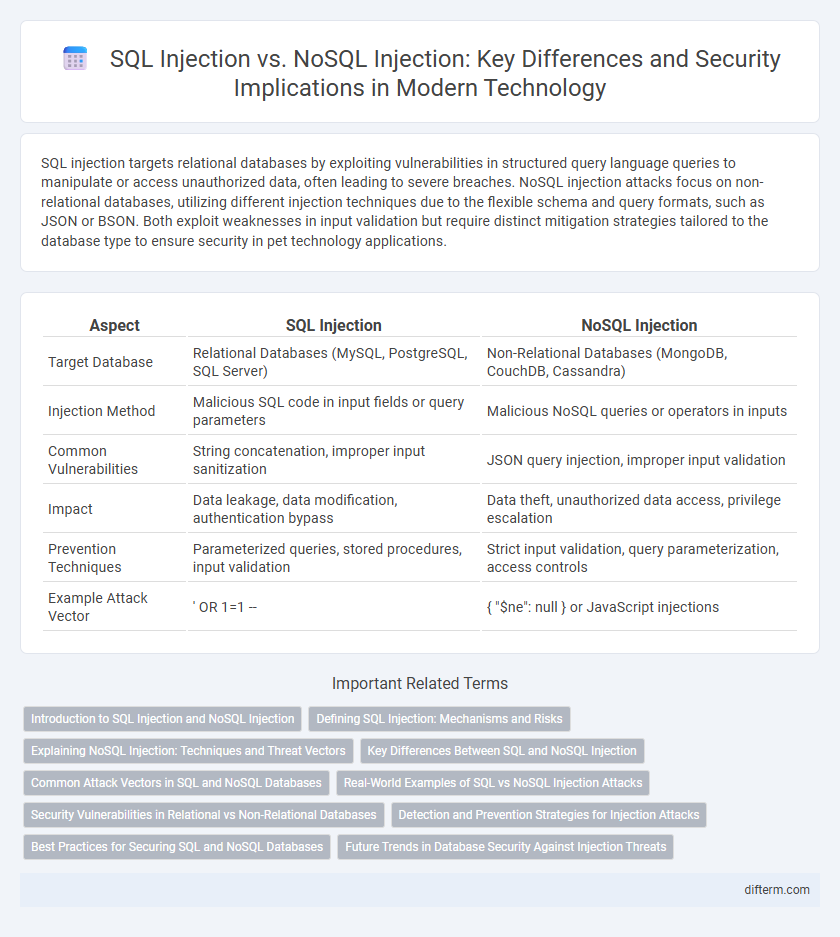
| Aspect | SQL Injection | NoSQL Injection |
|---|---|---|
| Target Database | Relational Databases (MySQL, PostgreSQL, SQL Server) | Non-Relational Databases (MongoDB, CouchDB, Cassandra) |
| Injection Method | Malicious SQL code in input fields or query parameters | Malicious NoSQL queries or operators in inputs |
| Common Vulnerabilities | String concatenation, improper input sanitization | JSON query injection, improper input validation |
| Impact | Data leakage, data modification, authentication bypass | Data theft, unauthorized data access, privilege escalation |
| Prevention Techniques | Parameterized queries, stored procedures, input validation | Strict input validation, query parameterization, access controls |
| Example Attack Vector | ' OR 1=1 -- | { "$ne": null } or JavaScript injections |
Introduction to SQL Injection and NoSQL Injection
SQL injection exploits vulnerabilities in traditional relational databases by inserting malicious SQL code into input fields to manipulate database queries and access unauthorized data. NoSQL injection targets non-relational databases like MongoDB or CouchDB, exploiting query structures unique to NoSQL systems to execute unauthorized commands or retrieve sensitive information. Understanding the differences in query languages and data models is essential for effective security measures against both SQL and NoSQL injection attacks.
Defining SQL Injection: Mechanisms and Risks
SQL Injection targets relational databases by exploiting improperly sanitized input fields to execute malicious SQL commands, allowing attackers to manipulate, steal, or delete sensitive data. It leverages vulnerabilities in structured query language syntax, enabling unauthorized access and control over database content. Common risks include data breaches, privilege escalation, and full database compromise in systems relying on traditional SQL databases.
Explaining NoSQL Injection: Techniques and Threat Vectors
NoSQL injection exploits vulnerabilities in non-relational databases by injecting malicious code into query structures, bypassing traditional SQL parsing. Common techniques involve exploiting unsanitized user inputs within JSON, XML, or JavaScript queries to manipulate database commands and retrieve unauthorized data. Threat vectors include injection into MongoDB, Cassandra, and CouchDB databases, where attackers leverage flexible query languages and schema-less formats to escalate privileges or exfiltrate sensitive information.
Key Differences Between SQL and NoSQL Injection
SQL injection targets relational databases by exploiting vulnerabilities in structured query language to manipulate or access sensitive data, whereas NoSQL injection affects non-relational databases like MongoDB by tampering with database queries or commands. SQL injection typically involves SQL statements within string inputs, while NoSQL injection leverages query operators or JSON-like structures to bypass authentication or retrieve unauthorized information. The fundamental difference lies in the database architecture and query languages, requiring distinct prevention techniques tailored to SQL or NoSQL environments.
Common Attack Vectors in SQL and NoSQL Databases
SQL injection commonly targets vulnerable input fields by injecting malicious SQL code through user inputs, exploiting improperly sanitized queries to manipulate relational databases. NoSQL injection attacks exploit unvalidated user input in query parameters or JSON objects, leveraging the flexible schema of NoSQL databases like MongoDB or CouchDB to execute unauthorized operations or retrieve sensitive data. Both attack vectors rely heavily on insufficient input validation and inadequate query parameter handling, emphasizing the need for robust security measures in database management systems.
Real-World Examples of SQL vs NoSQL Injection Attacks
SQL injection attacks exploit vulnerabilities in traditional relational databases like MySQL and SQL Server, often targeting login forms or search fields to manipulate queries and gain unauthorized access, as seen in the 2014 Sony Pictures breach. NoSQL injection attacks affect databases such as MongoDB and Couchbase, leveraging JSON-based query structures to inject malicious code, exemplified by the 2016 MongoDB ransom attacks that encrypted vital data. Both attack types demonstrate the critical need for input validation and parameterized queries to protect against breaches in their respective database technologies.
Security Vulnerabilities in Relational vs Non-Relational Databases
SQL injection targets relational databases by exploiting vulnerabilities in structured query language, allowing attackers to manipulate or access unauthorized data through malicious input. NoSQL injection affects non-relational databases, exploiting weaknesses in query interfaces or improper input validation, which can result in unauthorized data retrieval or command execution. Both injection types highlight critical security gaps in data sanitization and access controls within relational and non-relational database systems.
Detection and Prevention Strategies for Injection Attacks
SQL injection detection involves monitoring query patterns and employing web application firewalls (WAFs) that parse and block anomalous SQL syntax, while NoSQL injection detection requires specialized tools to analyze JSON query payloads for irregularities. Prevention strategies for SQL injection emphasize the use of prepared statements and parameterized queries to sanitize inputs, whereas NoSQL injection defense focuses on validating and escaping user inputs within document-based queries. Employing security frameworks that enforce strict input validation and routinely updating database drivers further mitigates risks associated with both injection attack types.
Best Practices for Securing SQL and NoSQL Databases
Implement parameterized queries and prepared statements to prevent SQL injection by separating code from data input in SQL databases. In NoSQL environments, validate and sanitize inputs rigorously to avoid injection attacks that exploit unstructured query languages. Employ role-based access control (RBAC) and regularly update database security patches to minimize vulnerabilities across both SQL and NoSQL systems.
Future Trends in Database Security Against Injection Threats
Emerging trends in database security emphasize adaptive machine learning algorithms designed to detect and mitigate SQL injection and NoSQL injection attacks in real time, enhancing anomaly detection beyond traditional signature-based methods. The integration of zero-trust architectures and advanced encryption techniques within cloud-native databases fortifies defenses against injection threats by minimizing attack surfaces and enforcing strict access controls. Future innovations focus on automated vulnerability scanning and AI-driven query analysis to proactively identify injection vectors, ensuring robust protection across diverse database technologies.
SQL injection vs NoSQL injection Infographic
 difterm.com
difterm.com