Symmetric encryption uses a single key for both encryption and decryption, offering faster performance and efficiency for large data volumes. Asymmetric encryption employs a pair of keys--public and private--enhancing security by enabling secure key exchange and digital signatures. Combining both methods often provides robust security solutions in modern technology applications.
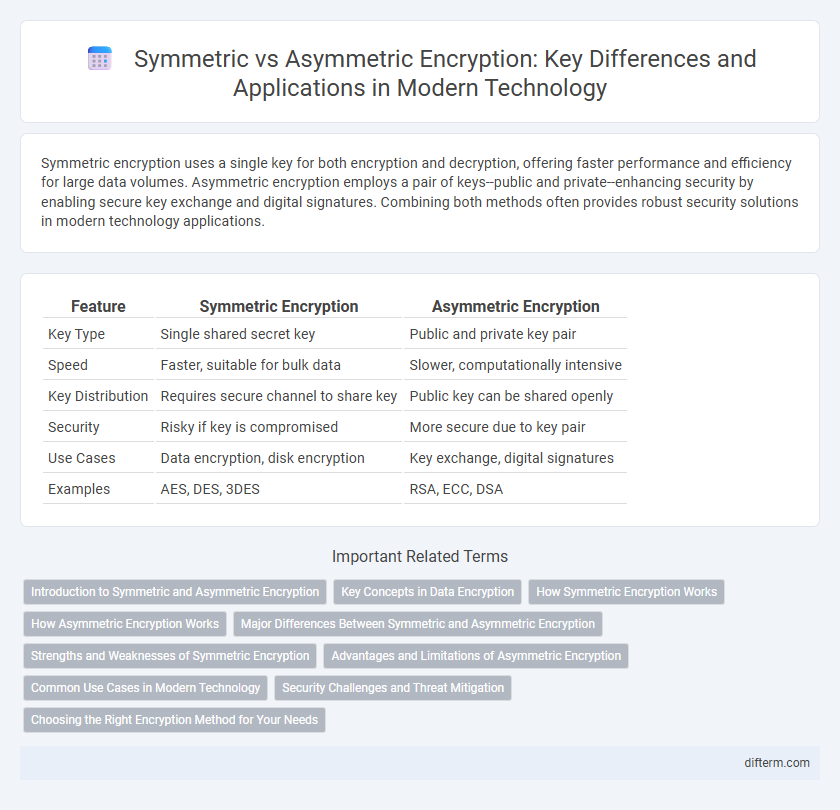
Table of Comparison
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Type | Single shared secret key | Public and private key pair |
| Speed | Faster, suitable for bulk data | Slower, computationally intensive |
| Key Distribution | Requires secure channel to share key | Public key can be shared openly |
| Security | Risky if key is compromised | More secure due to key pair |
| Use Cases | Data encryption, disk encryption | Key exchange, digital signatures |
| Examples | AES, DES, 3DES | RSA, ECC, DSA |
Introduction to Symmetric and Asymmetric Encryption
Symmetric encryption uses a single secret key for both encryption and decryption, ensuring fast and efficient data protection ideal for large datasets. Asymmetric encryption employs a pair of keys, a public key for encryption and a private key for decryption, enhancing security by enabling secure key exchange over insecure channels. The choice between symmetric and asymmetric encryption depends on the use case, balancing speed, security, and key management complexities.
Key Concepts in Data Encryption
Symmetric encryption uses a single secret key for both encryption and decryption, making it faster and efficient for large data volumes but requiring secure key distribution. Asymmetric encryption relies on a pair of keys--a public key for encryption and a private key for decryption--enabling secure communication without sharing secret keys. Both methods are fundamental in data encryption, with symmetric encryption often used for speed and asymmetric for secure key exchange and digital signatures.
How Symmetric Encryption Works
Symmetric encryption works by using a single secret key to both encrypt and decrypt data, ensuring confidentiality through efficient and fast cryptographic algorithms like AES or DES. The sender and receiver must securely share this key beforehand, as the same key is required to transform plaintext into ciphertext and back. This method is widely used in applications requiring high-speed data encryption, such as secure file storage, VPNs, and real-time communications.
How Asymmetric Encryption Works
Asymmetric encryption uses a pair of keys--public and private--to secure data, where the public key encrypts the information and only the corresponding private key can decrypt it, ensuring secure communication without sharing private keys. This method relies on complex mathematical algorithms, such as RSA or ECC, to generate keys that are computationally infeasible to reverse-engineer. Its design enhances digital security by enabling authentication, data integrity, and confidentiality in technologies like SSL/TLS and email encryption.
Major Differences Between Symmetric and Asymmetric Encryption
Symmetric encryption uses a single secret key for both encryption and decryption, providing faster processing and lower computational overhead, which makes it ideal for encrypting large amounts of data. Asymmetric encryption employs a pair of mathematically related keys--a public key for encryption and a private key for decryption--enabling secure key exchange and digital signatures, but at the cost of slower performance due to complex algorithms like RSA or ECC. The fundamental difference lies in key management: symmetric encryption requires secure key distribution, while asymmetric encryption simplifies secure communication channels by eliminating the need to share private keys.
Strengths and Weaknesses of Symmetric Encryption
Symmetric encryption excels in speed and efficiency, making it ideal for encrypting large volumes of data in real-time applications such as database encryption and secure communications. Its primary weakness lies in key distribution and management, as both sender and receiver must securely share the same secret key, increasing vulnerability to interception or unauthorized access. Despite this, symmetric algorithms like AES remain highly secure against brute-force attacks when using sufficiently long keys, sustaining their widespread use in various cybersecurity practices.
Advantages and Limitations of Asymmetric Encryption
Asymmetric encryption enhances security by using a pair of public and private keys, enabling secure key exchange and digital signatures without the need to share secret keys. Its main advantage lies in providing strong authentication and non-repudiation, crucial for secure communications and identity verification. However, asymmetric encryption is computationally intensive and slower than symmetric encryption, which limits its efficiency for encrypting large volumes of data.
Common Use Cases in Modern Technology
Symmetric encryption is widely used in securing large volumes of data during transmission and storage due to its speed and efficiency, making it ideal for encrypting databases, files, and VPN communications. Asymmetric encryption, utilizing public and private keys, is crucial for secure key exchange, digital signatures, and authentication in protocols like SSL/TLS and email encryption. Modern technology often combines both methods in hybrid encryption systems to balance security and performance, typically using asymmetric encryption to share symmetric keys.
Security Challenges and Threat Mitigation
Symmetric encryption relies on a single key for both encryption and decryption, posing significant security challenges such as key distribution and management vulnerabilities, which can be exploited through interception or replication. Asymmetric encryption utilizes a pair of public and private keys, enhancing security by eliminating the need for shared secret keys but introduces computational overhead and susceptibility to man-in-the-middle attacks if public keys are not properly verified. Effective threat mitigation involves implementing hybrid encryption schemes that leverage the speed of symmetric algorithms and the secure key exchange of asymmetric methods, alongside robust key management protocols and digital certificate validation.
Choosing the Right Encryption Method for Your Needs
Symmetric encryption offers faster processing and is ideal for encrypting large amounts of data, making it suitable for internal communications and real-time applications. Asymmetric encryption provides enhanced security through the use of public and private keys, which is essential for secure key exchange, digital signatures, and protecting data in transit over untrusted networks. Selecting the right encryption method depends on the specific use case, balancing speed, security requirements, and the nature of the data being protected.
Symmetric encryption vs Asymmetric encryption Infographic
 difterm.com
difterm.com