Red teaming simulates cyberattacks to identify vulnerabilities by adopting the perspective of potential adversaries, rigorously testing security defenses. Blue teaming involves defending against such attacks by monitoring, detecting, and responding to threats in real time, ensuring robust protection and incident recovery. Both teams collaborate to strengthen an organization's cybersecurity posture by continuously refining attack and defense strategies.
Table of Comparison
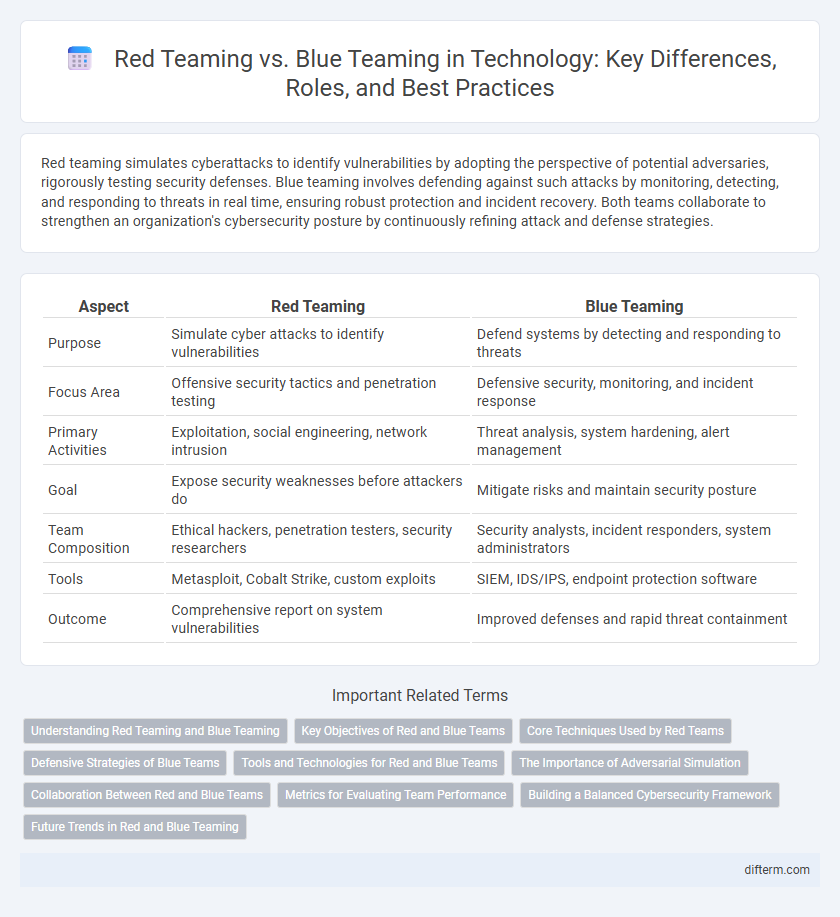
| Aspect | Red Teaming | Blue Teaming |
|---|---|---|
| Purpose | Simulate cyber attacks to identify vulnerabilities | Defend systems by detecting and responding to threats |
| Focus Area | Offensive security tactics and penetration testing | Defensive security, monitoring, and incident response |
| Primary Activities | Exploitation, social engineering, network intrusion | Threat analysis, system hardening, alert management |
| Goal | Expose security weaknesses before attackers do | Mitigate risks and maintain security posture |
| Team Composition | Ethical hackers, penetration testers, security researchers | Security analysts, incident responders, system administrators |
| Tools | Metasploit, Cobalt Strike, custom exploits | SIEM, IDS/IPS, endpoint protection software |
| Outcome | Comprehensive report on system vulnerabilities | Improved defenses and rapid threat containment |
Understanding Red Teaming and Blue Teaming
Red Teaming involves ethical hackers simulating cyberattacks to identify vulnerabilities within an organization's security infrastructure, providing a proactive approach to threat detection. Blue Teaming focuses on defending against these attacks by monitoring systems, analyzing threats, and implementing robust security measures to mitigate risks in real-time. Understanding the interplay between Red and Blue Teams enhances an organization's resilience through continuous assessment and fortified defense strategies.
Key Objectives of Red and Blue Teams
Red teams focus on simulating real-world cyberattacks to identify vulnerabilities and test the effectiveness of security measures, aiming to expose weaknesses before malicious actors can exploit them. Blue teams concentrate on monitoring, detecting, and responding to security incidents to protect organizational assets and minimize damage during attacks. The key objectives of red teams revolve around offensive strategies and penetration testing, while blue teams emphasize defensive tactics, incident response, and continuous improvement of security posture.
Core Techniques Used by Red Teams
Red teams employ core techniques such as social engineering, vulnerability exploitation, and advanced persistent threat simulations to identify security weaknesses. They utilize penetration testing tools, custom malware, and network reconnaissance to mimic real-world cyberattacks. These offensive methodologies enable organizations to assess the effectiveness of their security posture and response capabilities.
Defensive Strategies of Blue Teams
Blue Teams implement robust defensive strategies including continuous network monitoring, threat hunting, and incident response protocols to identify and mitigate cybersecurity threats proactively. They deploy advanced tools such as intrusion detection systems (IDS), endpoint detection and response (EDR), and Security Information and Event Management (SIEM) platforms to enhance situational awareness and strengthen defense mechanisms. Emphasizing vulnerability management and regular security assessments enables Blue Teams to maintain resilient infrastructure against sophisticated cyber attacks simulated by Red Teams.
Tools and Technologies for Red and Blue Teams
Red teams utilize advanced penetration testing frameworks like Metasploit, Cobalt Strike, and custom exploit development tools to simulate sophisticated attacks and identify vulnerabilities. Blue teams employ Security Information and Event Management (SIEM) systems such as Splunk, QRadar, and Endpoint Detection and Response (EDR) solutions like CrowdStrike or Carbon Black to detect, analyze, and respond to security incidents in real-time. Integration of threat intelligence platforms and automated response tools enhances both teams' capabilities in proactive defense and attack simulation.
The Importance of Adversarial Simulation
Adversarial simulation plays a critical role in cybersecurity through red teaming and blue teaming exercises, enabling organizations to identify vulnerabilities and enhance defense mechanisms. Red teams simulate real-world cyberattacks to expose weaknesses, while blue teams focus on detecting, responding to, and mitigating these attacks. This proactive approach strengthens overall security posture by improving threat detection capabilities and fostering continuous improvement in incident response strategies.
Collaboration Between Red and Blue Teams
Collaboration between Red and Blue Teams enhances cybersecurity by enabling comprehensive threat identification and mitigation. Red Teams simulate real-world attacks, providing valuable insights into vulnerabilities, while Blue Teams use this intelligence to strengthen defenses and improve incident response. Continuous communication and shared knowledge between these teams drive proactive security measures and resilience against evolving cyber threats.
Metrics for Evaluating Team Performance
Red teaming performance metrics include the number of successful exploitations, time taken to breach defenses, and coverage of attack surface simulated. Blue team effectiveness is measured by detection rate, mean time to detect (MTTD), mean time to respond (MTTR), and the ability to contain and remediate threats promptly. Combining quantitative data such as intrusion detection accuracy and incident response speed provides a comprehensive assessment of each team's operational impact in cybersecurity exercises.
Building a Balanced Cybersecurity Framework
Red teaming simulates real-world cyberattacks by identifying vulnerabilities through adversarial methods, while blue teaming concentrates on defending systems by monitoring, detecting, and responding to threats. Integrating red and blue teams enhances an organization's cybersecurity posture by continuously testing defenses and refining incident response strategies. A balanced cybersecurity framework leverages the proactive attack simulations of red teams alongside the resilience-building measures of blue teams to minimize risk and improve threat mitigation.
Future Trends in Red and Blue Teaming
Future trends in red teaming emphasize the integration of artificial intelligence and machine learning to enhance threat simulation and vulnerability detection. Blue teaming advancements focus on leveraging real-time analytics and automated response systems to strengthen defense mechanisms and reduce incident response times. Collaborative platforms that facilitate continuous feedback loops between red and blue teams are becoming essential for adaptive cybersecurity strategies.
Red teaming vs Blue teaming Infographic
 difterm.com
difterm.com