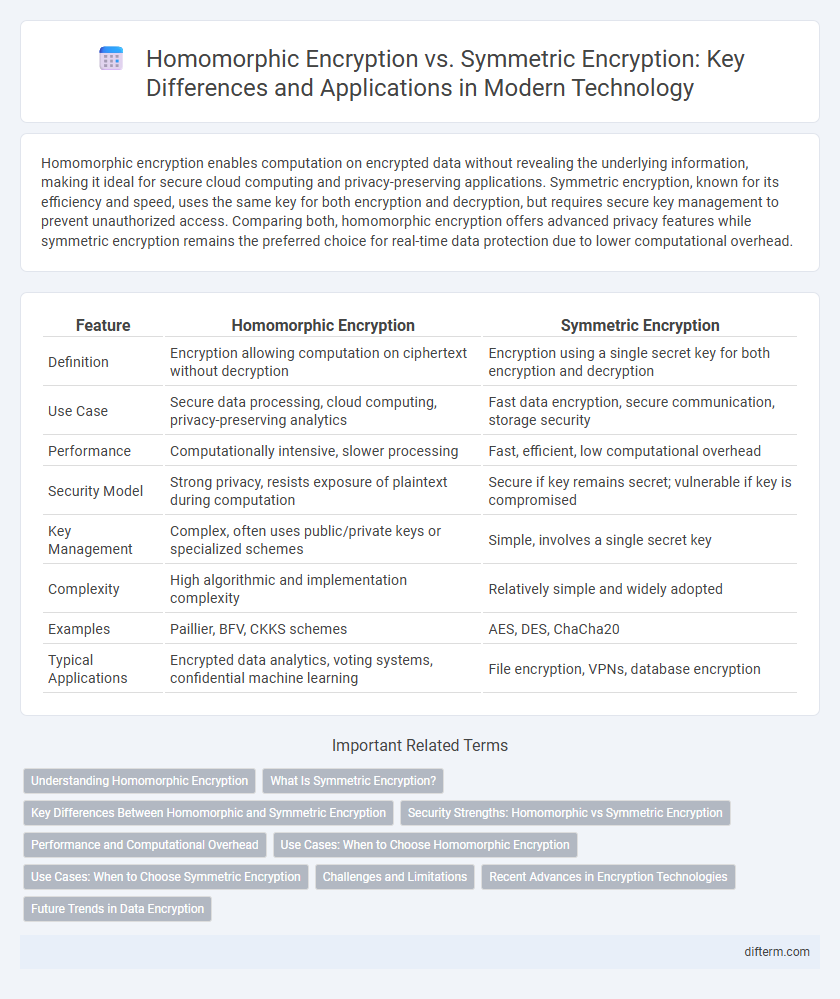
Homomorphic encryption enables computation on encrypted data without revealing the underlying information, making it ideal for secure cloud computing and privacy-preserving applications. Symmetric encryption, known for its efficiency and speed, uses the same key for both encryption and decryption, but requires secure key management to prevent unauthorized access. Comparing both, homomorphic encryption offers advanced privacy features while symmetric encryption remains the preferred choice for real-time data protection due to lower computational overhead.
Table of Comparison
| Feature | Homomorphic Encryption | Symmetric Encryption |
|---|---|---|
| Definition | Encryption allowing computation on ciphertext without decryption | Encryption using a single secret key for both encryption and decryption |
| Use Case | Secure data processing, cloud computing, privacy-preserving analytics | Fast data encryption, secure communication, storage security |
| Performance | Computationally intensive, slower processing | Fast, efficient, low computational overhead |
| Security Model | Strong privacy, resists exposure of plaintext during computation | Secure if key remains secret; vulnerable if key is compromised |
| Key Management | Complex, often uses public/private keys or specialized schemes | Simple, involves a single secret key |
| Complexity | High algorithmic and implementation complexity | Relatively simple and widely adopted |
| Examples | Paillier, BFV, CKKS schemes | AES, DES, ChaCha20 |
| Typical Applications | Encrypted data analytics, voting systems, confidential machine learning | File encryption, VPNs, database encryption |
Understanding Homomorphic Encryption
Homomorphic encryption enables computations on encrypted data without requiring decryption, preserving privacy while allowing complex data processing. Unlike symmetric encryption, which uses a single key for both encryption and decryption, homomorphic encryption supports secure data manipulation by performing operations directly on ciphertexts. This capability is crucial for secure cloud computing, enabling data analysis and machine learning on sensitive information without exposing raw data.
What Is Symmetric Encryption?
Symmetric encryption is a cryptographic method where the same secret key is used for both data encryption and decryption, enabling fast and efficient processing ideal for large data volumes. It relies on shared secret keys, making secure key distribution critical to prevent unauthorized access. Common symmetric encryption algorithms include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and Blowfish, widely used for securing communication channels and data storage.
Key Differences Between Homomorphic and Symmetric Encryption
Homomorphic encryption enables computation on encrypted data without decryption, preserving privacy during processing, while symmetric encryption requires data decryption before any operations, relying on a shared secret key. Key differences include the ability of homomorphic encryption to support complex mathematical operations on ciphertext, contrasted with symmetric encryption's faster performance but limited to data confidentiality during transmission or storage. These distinctions make homomorphic encryption suitable for secure cloud computing, whereas symmetric encryption is optimal for real-time data protection and resource-constrained environments.
Security Strengths: Homomorphic vs Symmetric Encryption
Homomorphic encryption enables computations on encrypted data without decryption, significantly enhancing data privacy and security in cloud computing and multi-party environments. Symmetric encryption offers faster processing speeds and strong security for data at rest and in transit but requires secure key management to prevent unauthorized access. The security strengths of homomorphic encryption lie in its ability to maintain data confidentiality during computation, while symmetric encryption excels in efficiency and simplicity for secure communication.
Performance and Computational Overhead
Homomorphic encryption enables computations on encrypted data without decryption, significantly increasing computational overhead compared to symmetric encryption, which offers faster processing due to simpler algorithms like AES. Symmetric encryption's performance excels in real-time applications with low latency requirements, while homomorphic encryption remains resource-intensive and slower, limiting its use to specific scenarios requiring data privacy during computation. Advances in homomorphic encryption schemes, such as BFV and CKKS, aim to reduce performance penalties but still fall short of the efficiency seen in symmetric encryption methods.
Use Cases: When to Choose Homomorphic Encryption
Homomorphic encryption excels in scenarios requiring computation on encrypted data without exposing sensitive information, such as secure cloud computing, privacy-preserving machine learning, and confidential data analytics. It enables collaborative data processing between parties without sharing raw data, critical for industries like healthcare, finance, and government where data privacy is paramount. Symmetric encryption, while efficient for secure storage and communication, cannot perform meaningful operations on encrypted data, limiting its use in privacy-preserving computations.
Use Cases: When to Choose Symmetric Encryption
Symmetric encryption is ideal for scenarios requiring high-speed data processing and large-volume encryption, such as securing communication channels, database encryption, and file storage. Its efficiency and lower computational overhead make it suitable for real-time applications like VPNs and disk encryption tools. In contrast to homomorphic encryption, symmetric encryption is preferred when performance and simplicity outweigh the need for secure computations on encrypted data.
Challenges and Limitations
Homomorphic encryption faces significant challenges in computational overhead and processing speed, limiting its practical application in real-time systems compared to symmetric encryption. Symmetric encryption, while efficient and fast due to simpler algorithms, suffers from key distribution and management vulnerabilities, restricting its scalability in complex environments. Both methods encounter trade-offs between security and performance, demanding careful selection based on specific use cases and operational constraints.
Recent Advances in Encryption Technologies
Recent advances in encryption technologies highlight significant progress in homomorphic encryption, enabling computations on encrypted data without decryption, thus enhancing data privacy in cloud computing and AI applications. Symmetric encryption algorithms, such as AES-256, continue to evolve with optimized hardware implementations and post-quantum resistance research, maintaining high-speed data protection standards. The integration of homomorphic encryption into real-world systems remains challenging due to computational overhead, whereas symmetric encryption offers efficient, established frameworks for secure communication.
Future Trends in Data Encryption
Homomorphic encryption enables computations on encrypted data without decryption, offering promising advances in secure data processing and cloud computing. Symmetric encryption remains efficient for fast, large-scale data protection but faces challenges in key distribution and management. Future trends emphasize integrating homomorphic encryption with traditional symmetric methods to balance performance and security in evolving digital ecosystems.
Homomorphic Encryption vs Symmetric Encryption Infographic
 difterm.com
difterm.com