OAuth2 is an authorization framework that enables third-party applications to obtain limited access to user resources without exposing credentials, while OpenID Connect builds on OAuth2 by adding an identity layer for user authentication. OpenID Connect provides ID tokens alongside OAuth2's access tokens, allowing applications to verify user identity and obtain profile information securely. Choosing between OAuth2 and OpenID Connect depends on whether the focus is solely on access delegation or also on user authentication and identity management.
Table of Comparison
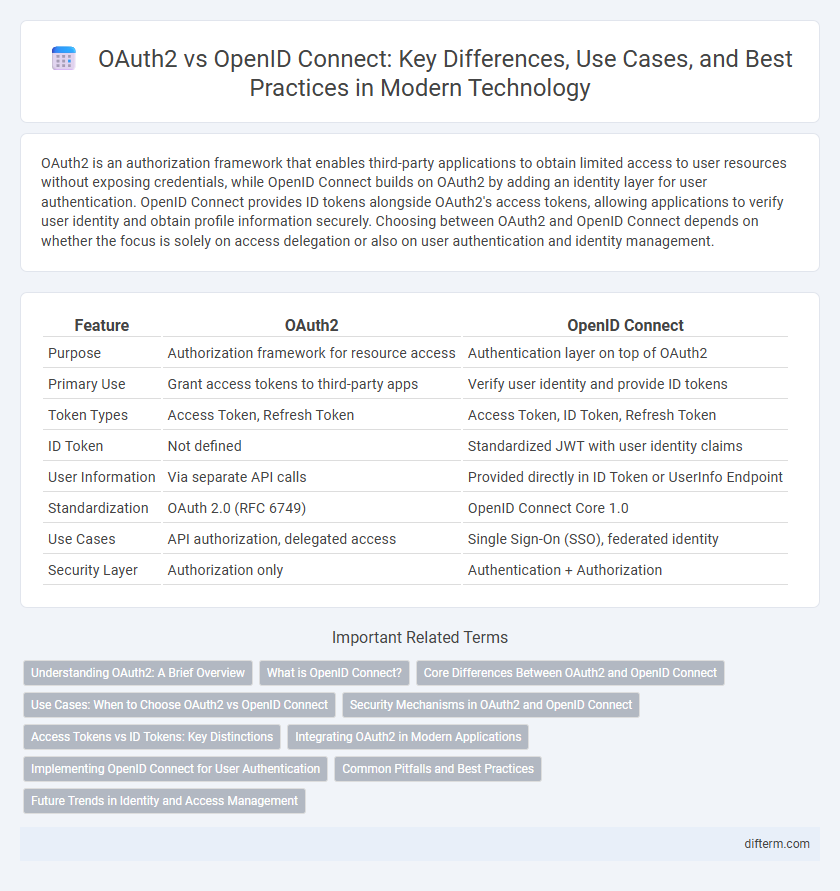
| Feature | OAuth2 | OpenID Connect |
|---|---|---|
| Purpose | Authorization framework for resource access | Authentication layer on top of OAuth2 |
| Primary Use | Grant access tokens to third-party apps | Verify user identity and provide ID tokens |
| Token Types | Access Token, Refresh Token | Access Token, ID Token, Refresh Token |
| ID Token | Not defined | Standardized JWT with user identity claims |
| User Information | Via separate API calls | Provided directly in ID Token or UserInfo Endpoint |
| Standardization | OAuth 2.0 (RFC 6749) | OpenID Connect Core 1.0 |
| Use Cases | API authorization, delegated access | Single Sign-On (SSO), federated identity |
| Security Layer | Authorization only | Authentication + Authorization |
Understanding OAuth2: A Brief Overview
OAuth2 is an authorization framework that enables applications to obtain limited access to user resources on a server without exposing user credentials. It defines four main roles: resource owner, client, authorization server, and resource server, facilitating secure delegated access using access tokens. OAuth2's versatility supports multiple grant types, including authorization code, implicit, client credentials, and resource owner password credentials, making it suitable for various application scenarios.
What is OpenID Connect?
OpenID Connect is an authentication layer built on top of the OAuth 2.0 protocol, enabling clients to verify the identity of end-users based on the authentication performed by an authorization server. It provides standardized identity tokens in JWT format, allowing seamless integration of secure single sign-on (SSO) and identity federation across web and mobile applications. OpenID Connect supports user profile data retrieval through its UserInfo endpoint, enhancing user authentication with detailed identity claims and improving security in distributed systems.
Core Differences Between OAuth2 and OpenID Connect
OAuth2 is an authorization framework designed to grant third-party applications limited access to user resources without exposing credentials, while OpenID Connect is an authentication layer built on top of OAuth2 that verifies user identity and provides basic profile information. OAuth2 primarily issues access tokens for resource access, whereas OpenID Connect introduces ID tokens containing user authentication details using JSON Web Tokens (JWT). The core difference lies in OAuth2's focus on delegated authorization and OpenID Connect's role in authentication and identity management.
Use Cases: When to Choose OAuth2 vs OpenID Connect
OAuth2 is ideal for authorization scenarios where secure delegated access to APIs or resources is needed without sharing user credentials, such as granting third-party apps permission to access a user's data. OpenID Connect is suitable for authentication use cases requiring user identity verification along with single sign-on (SSO) capabilities, making it a preferred choice for login flows in web and mobile applications. Choosing between OAuth2 and OpenID Connect depends on whether the primary objective is access delegation or user authentication.
Security Mechanisms in OAuth2 and OpenID Connect
OAuth2 provides authorization by issuing access tokens to third-party applications without exposing user credentials, utilizing bearer tokens and scopes to limit access. OpenID Connect builds on OAuth2 by adding an identity layer with ID tokens, which are JSON Web Tokens (JWT) signed using algorithms like RS256 for verifying user authentication. Both protocols employ secure token exchange mechanisms, but OpenID Connect enhances security through standardized user identity claims and nonce parameters to mitigate replay attacks.
Access Tokens vs ID Tokens: Key Distinctions
Access Tokens in OAuth2 are designed to grant access to protected resources by API servers, carrying scopes and permissions without revealing user identity. ID Tokens in OpenID Connect provide verified identity information about the user, including authentication details and user profile data, encoded in a JSON Web Token (JWT). Understanding the distinct roles of Access Tokens for authorization and ID Tokens for authentication is crucial for implementing secure and effective identity management systems.
Integrating OAuth2 in Modern Applications
Integrating OAuth2 in modern applications ensures secure authorization by granting limited access tokens without exposing user credentials, streamlining permission management across APIs and services. OAuth2's flexible framework supports diverse grant types, enabling seamless third-party integrations and enhanced user experience in mobile and web apps. Developers prioritize OAuth2 for robust access delegation, while OpenID Connect builds on OAuth2 by adding identity verification and standardizing user authentication flows.
Implementing OpenID Connect for User Authentication
Implementing OpenID Connect for user authentication enhances security by building upon OAuth2's authorization framework to provide identity verification through ID tokens. This approach enables seamless single sign-on (SSO) experiences while supporting user profile retrieval via standardized claims, ensuring interoperability across diverse applications. Developers benefit from improved token validation and reduced complexity, facilitating robust authentication flows in modern web and mobile environments.
Common Pitfalls and Best Practices
OAuth2 often faces common pitfalls such as insufficient token validation and improper scope management, which can lead to security vulnerabilities like token leakage and privilege escalation. OpenID Connect mitigates these risks by incorporating identity layer protocols and ID token validation, but developers must still enforce strict audience checks and secure nonce usage. Best practices include using standardized libraries, implementing robust token expiration and revocation policies, and regularly auditing authorization flows to prevent common misconfigurations.
Future Trends in Identity and Access Management
OAuth2 and OpenID Connect continue to evolve with increasing emphasis on decentralized identity frameworks and enhanced user privacy protections. Future trends in Identity and Access Management (IAM) highlight integration of biometric authentication and AI-driven risk analysis to strengthen security and streamline access. Enhanced interoperability between OAuth2 and OpenID Connect protocols promises more seamless, secure, and user-centric identity verification across diverse platforms.
OAuth2 vs OpenID Connect Infographic
 difterm.com
difterm.com