Zero-trust security eliminates implicit trust by continuously verifying every user and device attempting to access resources, enhancing protection against internal and external threats. Perimeter security relies on established boundaries and firewalls to block unauthorized access, but it struggles with modern cloud-based environments and remote workforces. Implementing zero-trust principles ensures a more adaptive and granular defense strategy, reducing the risk of breaches even if perimeter defenses are compromised.
Table of Comparison
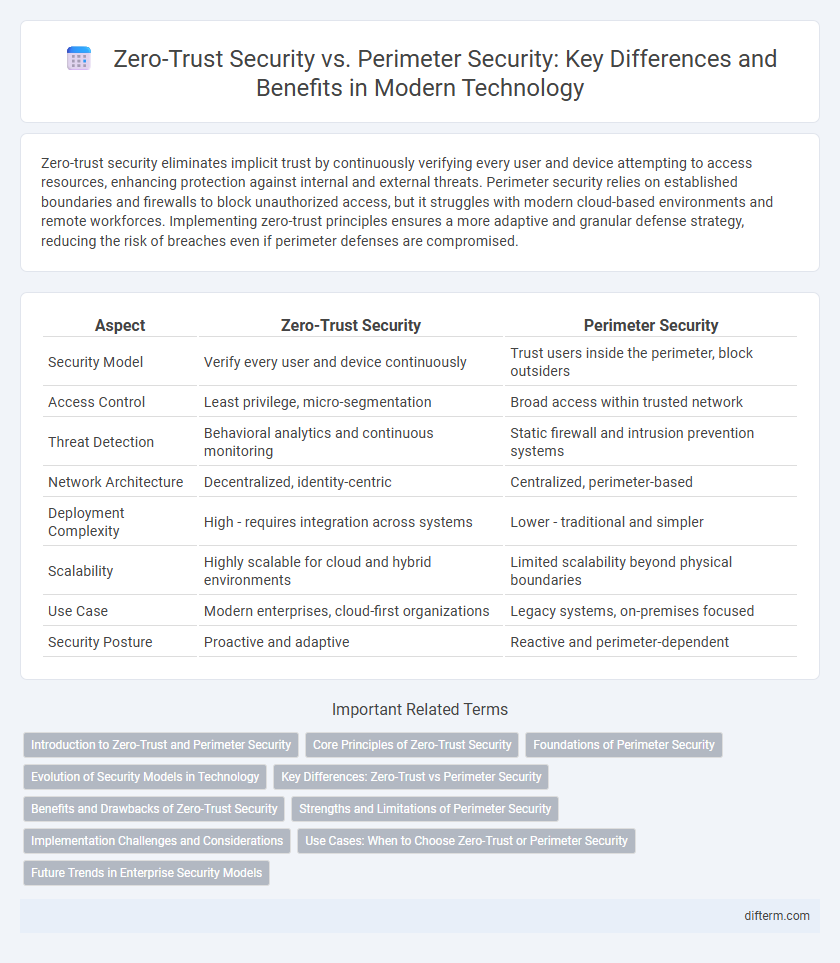
| Aspect | Zero-Trust Security | Perimeter Security |
|---|---|---|
| Security Model | Verify every user and device continuously | Trust users inside the perimeter, block outsiders |
| Access Control | Least privilege, micro-segmentation | Broad access within trusted network |
| Threat Detection | Behavioral analytics and continuous monitoring | Static firewall and intrusion prevention systems |
| Network Architecture | Decentralized, identity-centric | Centralized, perimeter-based |
| Deployment Complexity | High - requires integration across systems | Lower - traditional and simpler |
| Scalability | Highly scalable for cloud and hybrid environments | Limited scalability beyond physical boundaries |
| Use Case | Modern enterprises, cloud-first organizations | Legacy systems, on-premises focused |
| Security Posture | Proactive and adaptive | Reactive and perimeter-dependent |
Introduction to Zero-Trust and Perimeter Security
Zero-trust security eliminates implicit trust by continuously verifying every user and device, regardless of their network location, enhancing protection against insider threats and sophisticated cyberattacks. Perimeter security relies on a defined boundary, using firewalls and gateways to control access between trusted internal networks and untrusted external environments. The shift towards zero-trust reflects growing complexity in modern IT infrastructures and the need for dynamic, identity-based access controls beyond traditional perimeter defenses.
Core Principles of Zero-Trust Security
Zero-trust security operates on the principle of "never trust, always verify," enforcing strict identity verification for every person and device attempting to access resources, regardless of their location within or outside the network perimeter. It employs continuous monitoring, least privilege access, and micro-segmentation to minimize attack surfaces and prevent lateral movement of threats. Unlike perimeter security that relies on fixed boundaries, zero-trust architecture assumes breaches are inevitable and prioritizes securing individual assets through dynamic, context-aware policies.
Foundations of Perimeter Security
Perimeter security relies on establishing a defined boundary around a network, using firewalls, intrusion detection systems, and access controls to prevent unauthorized entry. This approach assumes that threats originate outside the trusted network and that internal users are reliable, which can create vulnerabilities if an attacker breaches the perimeter. Effective perimeter security depends on robust network segmentation and continuous monitoring to detect and respond to potential intrusions.
Evolution of Security Models in Technology
Zero-trust security represents an evolution from traditional perimeter security by eliminating implicit trust within networks and enforcing strict identity verification for every user and device. Unlike perimeter security, which relies on network boundaries to protect assets, zero-trust architecture continuously monitors and validates access, minimizing attack surfaces. This shift reflects the growing complexity of technology environments, driven by cloud adoption, mobile workforces, and sophisticated cyber threats.
Key Differences: Zero-Trust vs Perimeter Security
Zero-trust security enforces strict identity verification for every user and device attempting to access resources, regardless of their location, eliminating implicit trust within the network. Perimeter security relies on defining a secure boundary and primarily focuses on protecting the network edge from external threats, assuming everything inside is trustworthy. Key differences include zero-trust's continuous authentication and micro-segmentation versus perimeter security's reliance on firewalls and VPNs to create barrier defenses.
Benefits and Drawbacks of Zero-Trust Security
Zero-trust security offers enhanced protection by verifying every user and device regardless of network location, minimizing risks of insider threats and lateral movement in cyberattacks. It provides granular access control and continuous monitoring, improving threat detection and response compared to perimeter security's reliance on a defined network boundary. However, zero-trust implementation can be complex, costly, and require significant changes to existing infrastructure and user workflows.
Strengths and Limitations of Perimeter Security
Perimeter security provides a strong initial defense by controlling access through firewalls and intrusion detection systems, effectively preventing unauthorized entry at network boundaries. However, it struggles with internal threats and sophisticated attacks that bypass perimeter defenses, as it assumes all internal users are trustworthy. This limited visibility inside the network makes perimeter security insufficient against modern, decentralized, and cloud-based environments.
Implementation Challenges and Considerations
Zero-trust security implementation faces challenges such as the complexity of continuous authentication, granular access controls, and integrating diverse legacy systems without compromising user experience. Perimeter security struggles with evolving network boundaries, inadequate internal threat detection, and the growing adoption of cloud services that diminish traditional firewall effectiveness. Organizations must consider scalability, real-time monitoring capabilities, and comprehensive policy enforcement to ensure robust protection in hybrid and distributed environments.
Use Cases: When to Choose Zero-Trust or Perimeter Security
Zero-trust security is ideal for organizations with distributed workforces and cloud-based applications, as it enforces strict identity verification regardless of the user's location. Perimeter security remains effective for businesses with centralized networks and clearly defined physical boundaries, protecting against external threats. Choosing between zero-trust and perimeter security depends on factors like network architecture, application access patterns, and risk tolerance levels.
Future Trends in Enterprise Security Models
Zero-trust security models are increasingly prioritized over traditional perimeter security as enterprises adopt continuous verification and micro-segmentation to mitigate insider threats and cloud vulnerabilities. Future trends indicate an integration of AI-driven analytics for dynamic access control and real-time threat detection, enhancing adaptive security postures. The shift toward hybrid and multi-cloud environments accelerates zero-trust adoption, emphasizing identity-centric frameworks over static perimeter defenses.
Zero-trust security vs Perimeter security Infographic
 difterm.com
difterm.com