DNS over HTTP (DoH) encrypts DNS queries within standard HTTPS traffic, enhancing privacy by masking DNS requests as regular web traffic and making it difficult for third parties to monitor or block them. DNS over TLS (DoT) secures DNS queries by establishing a dedicated TLS connection, providing robust encryption and preventing eavesdropping, but it uses a separate port, which can be more easily identified and potentially blocked by network filters. Both protocols improve security over traditional DNS, but DoH offers greater stealth by blending with regular HTTPS traffic, while DoT provides a more straightforward, dedicated security layer for DNS resolution.
Table of Comparison
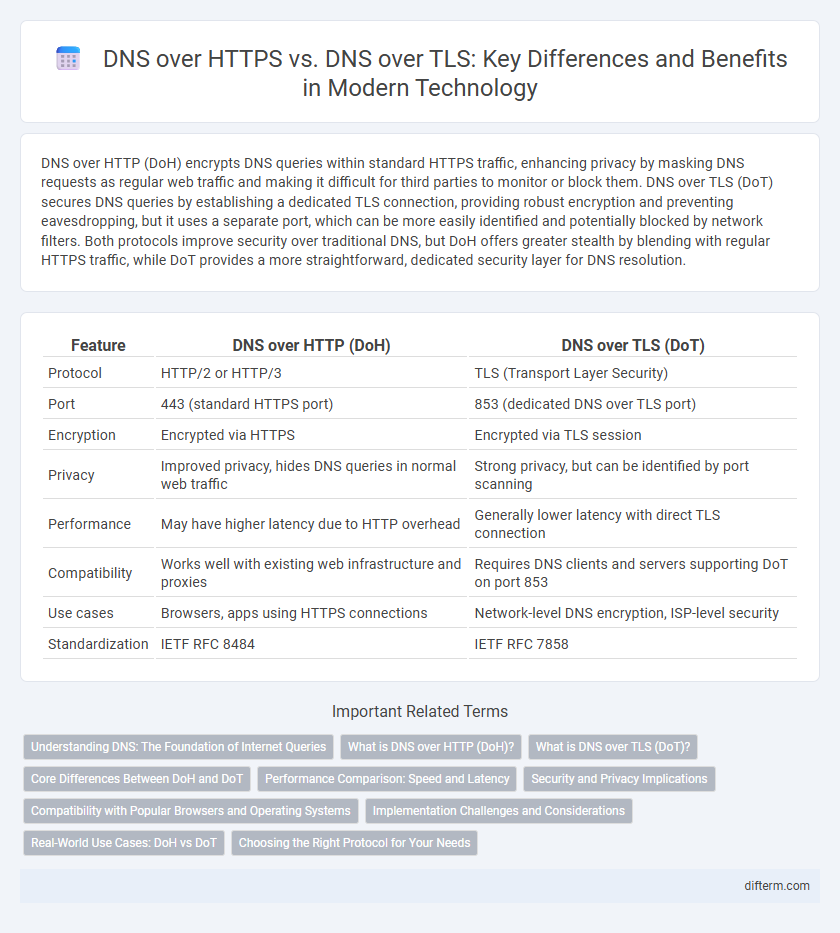
| Feature | DNS over HTTP (DoH) | DNS over TLS (DoT) |
|---|---|---|
| Protocol | HTTP/2 or HTTP/3 | TLS (Transport Layer Security) |
| Port | 443 (standard HTTPS port) | 853 (dedicated DNS over TLS port) |
| Encryption | Encrypted via HTTPS | Encrypted via TLS session |
| Privacy | Improved privacy, hides DNS queries in normal web traffic | Strong privacy, but can be identified by port scanning |
| Performance | May have higher latency due to HTTP overhead | Generally lower latency with direct TLS connection |
| Compatibility | Works well with existing web infrastructure and proxies | Requires DNS clients and servers supporting DoT on port 853 |
| Use cases | Browsers, apps using HTTPS connections | Network-level DNS encryption, ISP-level security |
| Standardization | IETF RFC 8484 | IETF RFC 7858 |
Understanding DNS: The Foundation of Internet Queries
DNS over HTTP (DoH) and DNS over TLS (DoT) both encrypt DNS queries to enhance privacy and security, preventing eavesdropping and tampering during internet communications. DoH transmits DNS requests through standard HTTPS ports, integrating seamlessly with web traffic, while DoT uses a dedicated port specifically for DNS encryption, ensuring clearly separated traffic channels. Understanding these protocols is crucial for optimizing internet query privacy, improving user security, and maintaining the integrity of DNS infrastructure.
What is DNS over HTTP (DoH)?
DNS over HTTP (DoH) is a protocol that encrypts DNS queries using the HTTPS protocol, enhancing user privacy and security by preventing eavesdropping and manipulation of DNS traffic. Unlike traditional DNS requests sent in plaintext, DoH leverages HTTP/2 or HTTP/3 to transmit DNS information securely over port 443, making it harder for attackers to intercept or block queries. Its adoption supports improved censorship resistance and integration with existing web infrastructure, contributing to a safer internet browsing experience.
What is DNS over TLS (DoT)?
DNS over TLS (DoT) is a security protocol that encrypts Domain Name System (DNS) queries and responses by using Transport Layer Security (TLS), thereby protecting DNS traffic from eavesdropping and tampering. Unlike traditional DNS, which sends unencrypted queries, DoT ensures confidentiality and data integrity between clients and DNS resolvers by leveraging the established security measures of TLS. This protocol operates typically over port 853, differentiating it from DNS over HTTP (DoH), which uses standard HTTPS ports and integrates DNS queries within web traffic.
Core Differences Between DoH and DoT
DNS over HTTP (DoH) encrypts DNS queries using the HTTPS protocol, embedding them within regular web traffic to enhance privacy and bypass censorship. DNS over TLS (DoT) secures DNS queries by establishing a dedicated TLS connection on port 853, focusing on encrypting DNS traffic separately from other internet activities. The core difference lies in their transport; DoH uses standard HTTPS ports (443) blending DNS with web traffic for stealth and flexibility, while DoT relies on a specific port offering streamlined DNS privacy without HTTP overhead.
Performance Comparison: Speed and Latency
DNS over HTTP (DoH) typically introduces higher latency compared to DNS over TLS (DoT) due to the additional overhead of HTTP/2 or HTTP/3 protocols, impacting speed in real-time applications. DoT uses a persistent TLS connection optimized solely for DNS queries, resulting in faster resolution times and lower latency under consistent network conditions. Performance benchmarks often show DoT outperforming DoH in speed-sensitive environments, while DoH offers greater compatibility with existing web infrastructure despite marginal speed trade-offs.
Security and Privacy Implications
DNS over HTTP (DoH) encrypts DNS queries within regular HTTPS traffic, enhancing privacy by preventing eavesdropping and manipulation by intermediaries, but it may centralize DNS resolution through fewer providers, raising concerns over data concentration. DNS over TLS (DoT) secures DNS queries by establishing a dedicated encrypted tunnel, offering robust protection against interception and spoofing while maintaining clear separation from standard HTTPS traffic for improved network management. Both protocols significantly enhance DNS security and privacy compared to traditional DNS, with DoH providing better integration with web traffic and DoT ensuring more transparent traffic handling and policy enforcement.
Compatibility with Popular Browsers and Operating Systems
DNS over HTTP (DoH) enjoys broad compatibility with popular browsers such as Mozilla Firefox, Google Chrome, and Microsoft Edge, as well as seamless integration across major operating systems including Windows, macOS, Linux, Android, and iOS. DNS over TLS (DoT) is natively supported by many operating systems like Android 9+ and certain Linux distributions but requires additional configuration or third-party apps on browsers and platforms that do not yet support it directly. The choice between DoH and DoT can significantly impact user experience and security, depending on device, browser support, and network environment.
Implementation Challenges and Considerations
DNS over HTTP (DoH) and DNS over TLS (DoT) both encrypt DNS queries to enhance privacy, but implementation challenges vary significantly. DoH integrates DNS traffic within standard HTTPS, complicating network traffic monitoring and filtering, while DoT operates on a dedicated port (853), making it easier to manage but more susceptible to blocking by firewalls. Considerations include performance impacts, compatibility with existing infrastructure, and ensuring robust certificate management to prevent man-in-the-middle attacks in both protocols.
Real-World Use Cases: DoH vs DoT
DNS over HTTP (DoH) is widely adopted in browsers and consumer applications to enhance privacy by encrypting DNS queries over standard HTTPS ports, effectively bypassing network restrictions and censorship. DNS over TLS (DoT) is preferred in enterprise environments and mobile networks for robust security, maintaining dedicated port 853 to ensure DNS traffic is separate from regular web traffic. Real-world deployments favor DoH for user-centric scenarios due to its ease of integration with existing web protocols, while DoT is ideal for network-level enforcement and management.
Choosing the Right Protocol for Your Needs
DNS over HTTPS (DoH) encrypts DNS queries within standard HTTPS traffic, enhancing privacy by preventing DNS query interception and manipulation, ideal for environments requiring robust anonymity and compatibility with existing web infrastructure. DNS over TLS (DoT) secures DNS queries through a dedicated encrypted TLS connection, offering better performance and simpler firewall management suitable for network-wide protection and enterprise settings. Selecting between DoH and DoT depends on specific needs for privacy, environment compatibility, and network management preferences.
DNS over HTTP vs DNS over TLS Infographic
 difterm.com
difterm.com