Certificate pinning enhances security by ensuring that a client only accepts a specific server certificate or public key, effectively preventing man-in-the-middle attacks even if a trusted certificate authority is compromised. HTTP Strict Transport Security (HSTS) instructs browsers to only communicate over HTTPS, reducing the risk of protocol downgrade attacks and cookie hijacking. While certificate pinning offers granular control over server authentication, HSTS provides broad enforcement of secure connections for all requests to a domain.
Table of Comparison
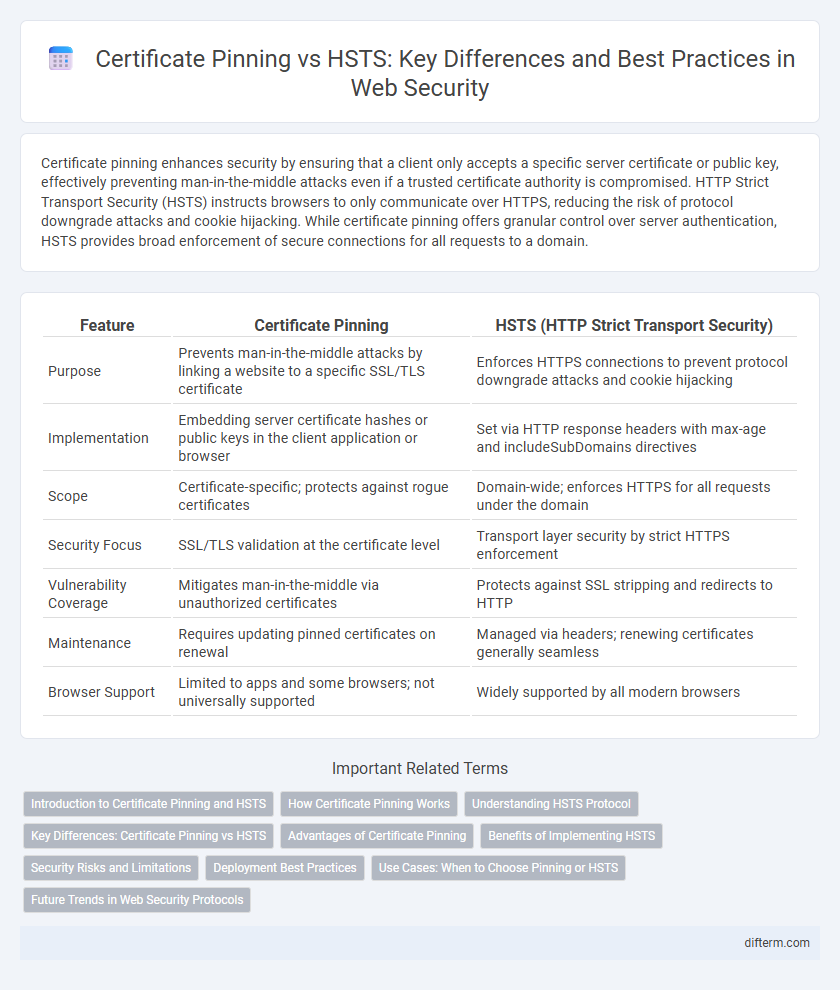
| Feature | Certificate Pinning | HSTS (HTTP Strict Transport Security) |
|---|---|---|
| Purpose | Prevents man-in-the-middle attacks by linking a website to a specific SSL/TLS certificate | Enforces HTTPS connections to prevent protocol downgrade attacks and cookie hijacking |
| Implementation | Embedding server certificate hashes or public keys in the client application or browser | Set via HTTP response headers with max-age and includeSubDomains directives |
| Scope | Certificate-specific; protects against rogue certificates | Domain-wide; enforces HTTPS for all requests under the domain |
| Security Focus | SSL/TLS validation at the certificate level | Transport layer security by strict HTTPS enforcement |
| Vulnerability Coverage | Mitigates man-in-the-middle via unauthorized certificates | Protects against SSL stripping and redirects to HTTP |
| Maintenance | Requires updating pinned certificates on renewal | Managed via headers; renewing certificates generally seamless |
| Browser Support | Limited to apps and some browsers; not universally supported | Widely supported by all modern browsers |
Introduction to Certificate Pinning and HSTS
Certificate pinning is a security technique that binds a service to specific cryptographic public keys, reducing the risk of man-in-the-middle attacks by ensuring the client only accepts a predetermined certificate. HTTP Strict Transport Security (HSTS) enforces secure HTTPS connections by instructing browsers to refuse insecure HTTP requests, preventing protocol downgrade attacks and cookie hijacking. Both methods enhance web communication security, with certificate pinning focusing on validation of trusted certificates and HSTS on enforcing secure transport protocols.
How Certificate Pinning Works
Certificate pinning works by associating a specific cryptographic public key with a server or domain, ensuring that only certificates matching the pinned key are accepted during TLS handshake. This technique prevents attackers from using fraudulent or compromised certificates issued by rogue certificate authorities, enhancing resistance against man-in-the-middle (MITM) attacks. Unlike HSTS, which enforces HTTPS connections, certificate pinning tightly controls certificate validation to establish a trusted, secure communication channel.
Understanding HSTS Protocol
HSTS (HTTP Strict Transport Security) enforces secure HTTPS connections by instructing browsers to refuse insecure HTTP requests, effectively preventing protocol downgrade attacks and cookie hijacking. Unlike certificate pinning, which validates specific SSL/TLS certificates to thwart man-in-the-middle attacks, HSTS ensures continuous secure connections by automatically redirecting all requests to HTTPS. Implementing HSTS through the Strict-Transport-Security header enhances website security and user trust by minimizing vulnerabilities associated with unencrypted HTTP traffic.
Key Differences: Certificate Pinning vs HSTS
Certificate pinning enhances security by associating a host with their expected SSL/TLS certificate, preventing man-in-the-middle attacks through certificate validation. HSTS enforces HTTPS connections by instructing browsers to only communicate over secure channels, mitigating protocol downgrade and cookie hijacking attacks. Key differences include certificate pinning's focus on verifying specific certificates, while HSTS ensures the use of secure transport protocols across all subsequent connections.
Advantages of Certificate Pinning
Certificate pinning enhances security by directly associating a specific cryptographic key with a server, effectively mitigating man-in-the-middle attacks even if a Certificate Authority is compromised. Unlike HSTS, which enforces HTTPS connections but relies on trusted CAs, pinning provides a stronger guarantee of the server's identity by bypassing third-party validation. This reduces the risk of fraudulent certificates and improves control over trusted credentials, making it a preferred approach for high-security applications.
Benefits of Implementing HSTS
HTTP Strict Transport Security (HSTS) enhances web security by enforcing HTTPS connections, preventing protocol downgrade attacks and cookie hijacking. It ensures browsers only communicate over secure TLS channels, reducing the risk of man-in-the-middle attacks. Implementing HSTS improves user trust and compliance with modern security standards without relying on complex certificate management.
Security Risks and Limitations
Certificate pinning mitigates man-in-the-middle attacks by ensuring a specific certificate or public key is used, but it risks connection failures if certificates change without updates, causing site access issues. HSTS enforces HTTPS connections to prevent downgrade attacks and cookie hijacking but does not protect against compromised certificate authorities or misissued certificates. Both methods enhance security but have limitations, requiring careful implementation and maintenance to avoid potential vulnerabilities.
Deployment Best Practices
Certificate pinning enhances security by binding a specific certificate or public key to an application, preventing man-in-the-middle attacks even if a certificate authority is compromised. HSTS (HTTP Strict Transport Security) instructs browsers to exclusively use HTTPS, protecting against protocol downgrade attacks and cookie hijacking. Best deployment practices recommend combining certificate pinning for rigorous endpoint authentication with HSTS to enforce secure transport layers, ensuring multi-layered defense without user experience interruption.
Use Cases: When to Choose Pinning or HSTS
Certificate pinning enhances security by binding a specific certificate or public key to an application, making it ideal for protecting mobile apps and APIs from man-in-the-middle attacks during certificate replacement or compromise. HTTP Strict Transport Security (HSTS) enforces HTTPS connections on browsers, preventing protocol downgrade attacks and cookie hijacking primarily for web applications. Choose pinning for high-security client-server communication where control over trust anchors is critical, while HSTS suits enforcing secure connections on websites to improve overall web security posture.
Future Trends in Web Security Protocols
Certificate pinning and HSTS both enhance web security by mitigating man-in-the-middle attacks, but future trends emphasize integrating these protocols with emerging technologies like zero trust architecture and quantum-resistant cryptography. Evolving web security protocols increasingly leverage machine learning algorithms for real-time threat detection and automated certificate management, improving resilience against sophisticated cyber threats. Adoption of decentralized trust models and blockchain-based certificate transparency logs are also shaping the next generation of robust, scalable web security solutions.
Certificate pinning vs HSTS Infographic
 difterm.com
difterm.com