JWT (JSON Web Token) serves as a compact, URL-safe method for securely transmitting information between parties as a JSON object, primarily used for authentication and information exchange. OAuth is an authorization framework that enables third-party applications to obtain limited access to user resources without sharing credentials, often employing tokens like JWT for access delegation. Understanding the distinction between JWT as a token format and OAuth as an authorization protocol is essential for implementing secure and scalable authentication systems.
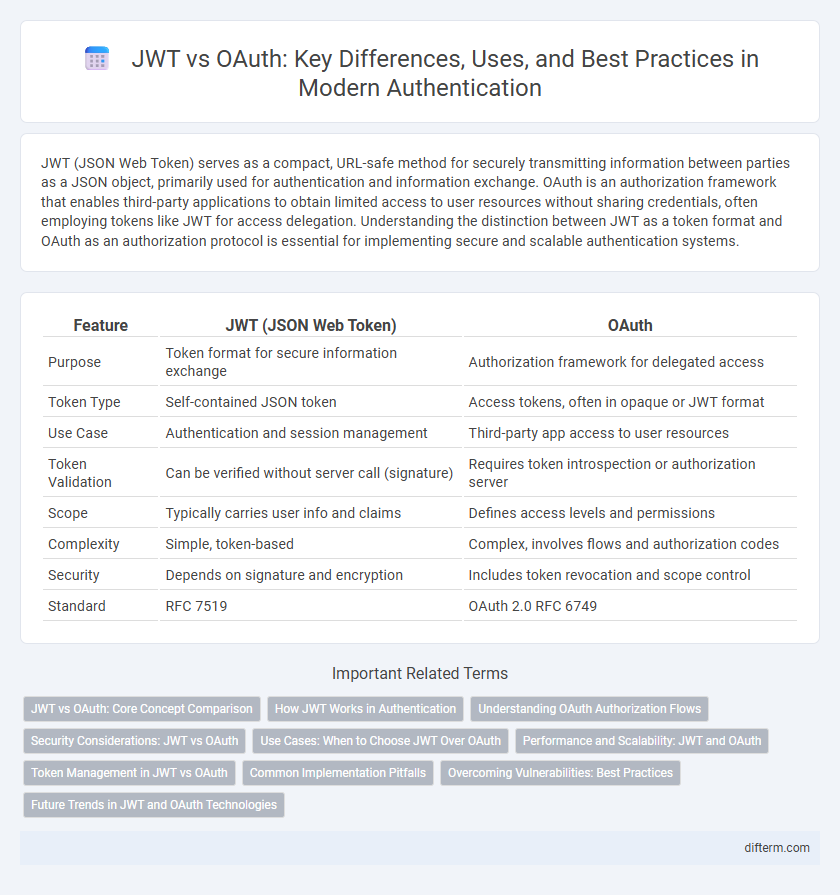
Table of Comparison
| Feature | JWT (JSON Web Token) | OAuth |
|---|---|---|
| Purpose | Token format for secure information exchange | Authorization framework for delegated access |
| Token Type | Self-contained JSON token | Access tokens, often in opaque or JWT format |
| Use Case | Authentication and session management | Third-party app access to user resources |
| Token Validation | Can be verified without server call (signature) | Requires token introspection or authorization server |
| Scope | Typically carries user info and claims | Defines access levels and permissions |
| Complexity | Simple, token-based | Complex, involves flows and authorization codes |
| Security | Depends on signature and encryption | Includes token revocation and scope control |
| Standard | RFC 7519 | OAuth 2.0 RFC 6749 |
JWT vs OAuth: Core Concept Comparison
JWT (JSON Web Token) is a compact, URL-safe token format used to securely transmit information between parties, primarily for authentication and information exchange. OAuth is an authorization framework that enables third-party applications to obtain limited access to user resources without sharing credentials, often leveraging JWT as a token format within its flows. While JWT serves as a token standard, OAuth defines the protocols and authorization processes governing token issuance and validation.
How JWT Works in Authentication
JWT (JSON Web Token) works in authentication by securely transmitting user information between parties as a JSON object that is digitally signed using a secret or public/private key pair. When a user logs in, the server generates a JWT containing claims such as user ID and expiration, which the client stores and includes in subsequent requests to verify identity without needing to query the database repeatedly. This stateless nature of JWT enhances scalability and performance in authentication workflows compared to traditional session management.
Understanding OAuth Authorization Flows
OAuth authorization flows define the protocols for granting limited access to user resources without exposing credentials, essential for secure third-party integrations. Common flows include Authorization Code, Implicit, Resource Owner Password Credentials, and Client Credentials, each tailored for different application types and security requirements. JWT (JSON Web Token) often serves as the token format within these flows, encapsulating user claims and permissions to enable stateless, scalable authentication and authorization.
Security Considerations: JWT vs OAuth
JWT (JSON Web Token) provides a compact and self-contained method for securely transmitting information between parties, with built-in signature verification to prevent tampering. OAuth, primarily used for authorization, leverages token exchange and scopes to limit access, enhancing security by delegating access rights without sharing credentials. Security considerations favor OAuth for complex, multi-service environments due to its dynamic access control, while JWT is optimal for stateless authentication where token verification and expiry management are critical.
Use Cases: When to Choose JWT Over OAuth
JWT excels in scenarios requiring stateless, compact, and self-contained tokens, making it ideal for single sign-on (SSO), API authentication, and mobile applications where minimizing server storage is crucial. OAuth is more suitable for delegated access scenarios, such as third-party application authorization, where resource owners grant limited access without sharing credentials. Choose JWT when simplicity, scalability, and direct token validation are priorities over complex permission scopes and multi-party authorization flows typical of OAuth.
Performance and Scalability: JWT and OAuth
JWT allows faster performance with stateless authentication by embedding user claims within the token, reducing server load and database queries. OAuth introduces more overhead due to token validation and authorization steps but offers superior scalability by delegating access control and supporting token revocation. Choosing JWT benefits applications requiring high throughput with minimal latency, whereas OAuth suits complex environments demanding granular permission management and secure delegation.
Token Management in JWT vs OAuth
JWT (JSON Web Token) enables stateless token management by encapsulating all user claims within the token, eliminating the need for server-side storage and facilitating scalable authentication. OAuth relies on access tokens, which often require server-side token storage and management for revocation, expiration, and refresh workflows, enabling granular control over user authorization scopes. JWT tokens can be self-contained and validated without database calls, whereas OAuth's token management provides enhanced security through centralized token lifecycle policies.
Common Implementation Pitfalls
Common implementation pitfalls in JWT versus OAuth often stem from improper token validation and insecure storage practices. Developers frequently expose JWTs to replay attacks by failing to implement expiration or audience checks, while OAuth implementations may incorrectly handle token scopes or redirect URIs, leading to unauthorized access. Ensuring rigorous validation mechanisms and adhering to security best practices mitigates vulnerabilities inherent in both JWT and OAuth frameworks.
Overcoming Vulnerabilities: Best Practices
To overcome vulnerabilities in JWT and OAuth implementations, enforce strict token expiration and use strong cryptographic algorithms like RS256 for signing tokens. Implement proper audience and issuer validation alongside secure storage practices such as HTTP-only cookies or encrypted local storage to prevent token theft. Regularly update libraries and conduct security audits to identify and remediate potential weaknesses within authentication flows.
Future Trends in JWT and OAuth Technologies
Emerging trends in JWT and OAuth technologies emphasize enhanced security measures such as zero-trust architecture and continuous authorization to combat evolving cyber threats. Integration with decentralized identity frameworks and blockchain is gaining traction, promoting more transparent and user-controlled authentication processes. Advances in AI-driven anomaly detection are also being incorporated to improve real-time threat analysis within JWT and OAuth workflows.
JWT vs OAuth Infographic
 difterm.com
difterm.com