SQL injection targets databases by inserting malicious SQL code to manipulate or retrieve sensitive information, posing a significant threat to data integrity. Cross-site scripting (XSS) exploits vulnerabilities in web applications to inject malicious scripts, compromising user interactions and session security. Both attacks require robust input validation and sanitization to protect web applications from unauthorized access and data breaches.
Table of Comparison
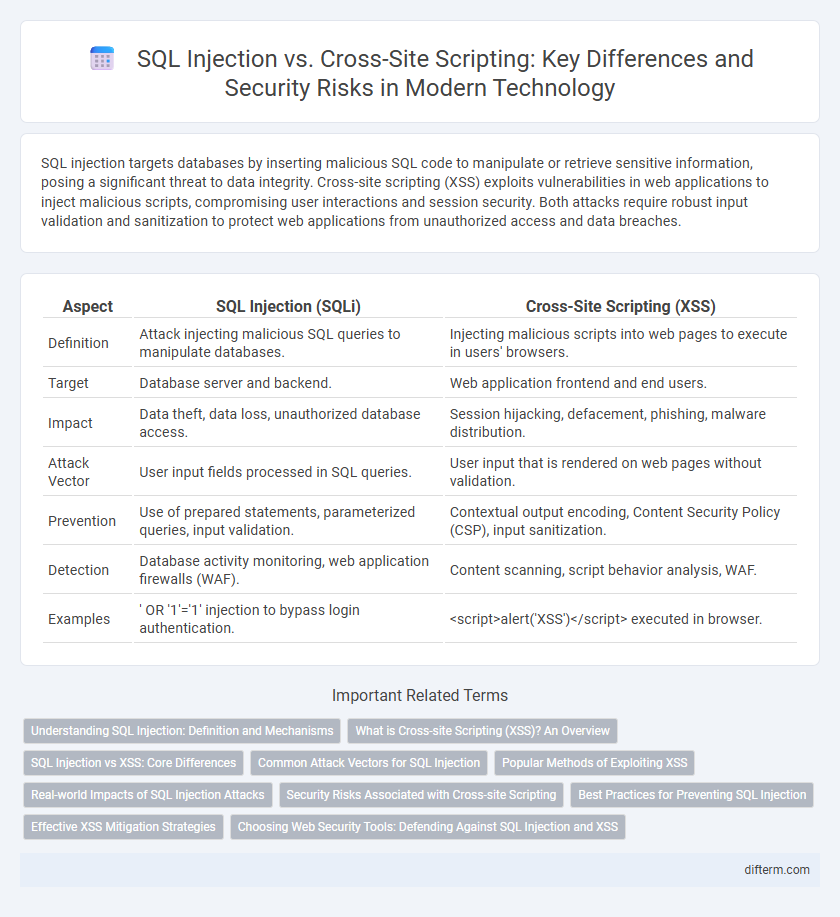
| Aspect | SQL Injection (SQLi) | Cross-Site Scripting (XSS) |
|---|---|---|
| Definition | Attack injecting malicious SQL queries to manipulate databases. | Injecting malicious scripts into web pages to execute in users' browsers. |
| Target | Database server and backend. | Web application frontend and end users. |
| Impact | Data theft, data loss, unauthorized database access. | Session hijacking, defacement, phishing, malware distribution. |
| Attack Vector | User input fields processed in SQL queries. | User input that is rendered on web pages without validation. |
| Prevention | Use of prepared statements, parameterized queries, input validation. | Contextual output encoding, Content Security Policy (CSP), input sanitization. |
| Detection | Database activity monitoring, web application firewalls (WAF). | Content scanning, script behavior analysis, WAF. |
| Examples | ' OR '1'='1' injection to bypass login authentication. | <script>alert('XSS')</script> executed in browser. |
Understanding SQL Injection: Definition and Mechanisms
SQL injection is a cyberattack technique where malicious actors exploit vulnerabilities in an application's SQL queries by injecting harmful code to manipulate database operations. This attack leverages improper input validation, allowing attackers to retrieve, alter, or delete sensitive data within relational databases such as MySQL, PostgreSQL, or SQL Server. Understanding the mechanisms of SQL injection involves recognizing how unescaped inputs in dynamic SQL statements create entry points for unauthorized data access and command execution.
What is Cross-site Scripting (XSS)? An Overview
Cross-site Scripting (XSS) is a security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users, exploiting the trust a user has in a particular website. Unlike SQL injection, which targets databases by manipulating query statements, XSS attacks aim to execute harmful client-side scripts to steal cookies, session tokens, or redirect users to malicious sites. XSS vulnerabilities typically arise from insufficient input validation and output encoding in web applications.
SQL Injection vs XSS: Core Differences
SQL Injection exploits vulnerabilities in database queries by injecting malicious SQL code to manipulate or access sensitive data, primarily targeting backend systems. Cross-Site Scripting (XSS) attacks inject malicious scripts into web pages viewed by other users, aiming to steal cookies, session tokens, or execute unauthorized actions on the client side. The core difference lies in SQL Injection compromising database integrity and XSS targeting client-side code execution for unauthorized data access or manipulation.
Common Attack Vectors for SQL Injection
SQL injection attacks primarily exploit vulnerabilities in web application input fields, such as login forms, search boxes, and URL parameters, enabling attackers to manipulate backend SQL queries. Attackers commonly use crafted inputs containing SQL code to bypass authentication, retrieve sensitive data, or modify database contents. Preventing SQL injection involves implementing parameterized queries, input validation, and using prepared statements to sanitize user input and restrict malicious commands.
Popular Methods of Exploiting XSS
Popular methods of exploiting Cross-site Scripting (XSS) include reflected XSS, stored XSS, and DOM-based XSS, each targeting different vectors to inject malicious scripts into web applications. Attackers exploit vulnerabilities by embedding harmful JavaScript code that executes in the victim's browser, enabling data theft, session hijacking, or phishing. Unlike SQL injection, which manipulates backend databases, XSS focuses on compromising client-side scripts and user interactions within compromised web pages.
Real-world Impacts of SQL Injection Attacks
SQL Injection attacks exploit vulnerabilities in database queries, enabling attackers to manipulate or extract sensitive data, often leading to severe data breaches and financial losses. These attacks have compromised major corporations, exposing millions of user credentials and personal information, resulting in long-lasting reputational damage and costly remediation efforts. Unlike Cross-site Scripting, which targets client-side code, SQL Injection directly assaults backend databases, amplifying the potential scale and impact of the attack.
Security Risks Associated with Cross-site Scripting
Cross-site scripting (XSS) poses significant security risks by allowing attackers to inject malicious scripts into web pages viewed by other users, potentially leading to data theft, session hijacking, and unauthorized access. Unlike SQL injection, which targets backend databases, XSS exploits client-side vulnerabilities to execute scripts within the user's browser environment. Effective prevention of XSS requires rigorous input validation, output encoding, and the implementation of Content Security Policy (CSP) headers.
Best Practices for Preventing SQL Injection
Best practices for preventing SQL injection include using prepared statements with parameterized queries to ensure user input is treated as data, not executable code. Employing strong input validation and escaping special characters further reduces the risk of malicious SQL code execution. Regularly updating database management systems and implementing least privilege access controls enhance overall security against injection attacks.
Effective XSS Mitigation Strategies
Effective XSS mitigation strategies include input validation, output encoding, and implementing Content Security Policy (CSP) to restrict script execution. Utilizing secure frameworks with built-in XSS protections and regularly updating software reduces vulnerabilities. Employing proper HTTP-only and secure cookie flags further prevents theft of session tokens through malicious scripts.
Choosing Web Security Tools: Defending Against SQL Injection and XSS
Selecting web security tools requires prioritizing capabilities that detect and mitigate SQL Injection and Cross-site Scripting (XSS) attacks effectively. Tools with advanced input validation, real-time code analysis, and comprehensive vulnerability scanning ensure protection against the injection of malicious SQL commands and the execution of unauthorized scripts. Integration with continuous monitoring and patch management also enhances defense mechanisms, reducing the risk of data breaches and reputation damage.
SQL injection vs Cross-site scripting Infographic
 difterm.com
difterm.com