Bcrypt offers superior security over SHA256 by incorporating a salt and being intentionally slower, which protects against brute-force attacks and rainbow table exploits. SHA256, while faster and efficient for checksum purposes, lacks built-in salting and is more vulnerable in password hashing contexts. Choosing Bcrypt enhances password protection through adaptive complexity, making it the preferred algorithm for secure authentication systems.
Table of Comparison
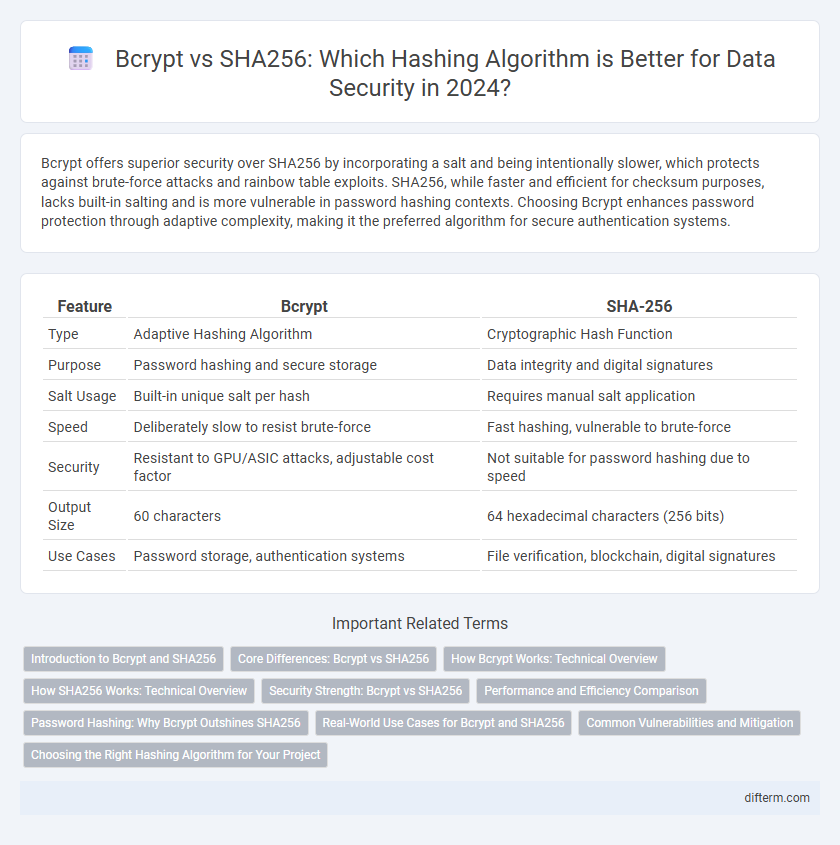
| Feature | Bcrypt | SHA-256 |
|---|---|---|
| Type | Adaptive Hashing Algorithm | Cryptographic Hash Function |
| Purpose | Password hashing and secure storage | Data integrity and digital signatures |
| Salt Usage | Built-in unique salt per hash | Requires manual salt application |
| Speed | Deliberately slow to resist brute-force | Fast hashing, vulnerable to brute-force |
| Security | Resistant to GPU/ASIC attacks, adjustable cost factor | Not suitable for password hashing due to speed |
| Output Size | 60 characters | 64 hexadecimal characters (256 bits) |
| Use Cases | Password storage, authentication systems | File verification, blockchain, digital signatures |
Introduction to Bcrypt and SHA256
Bcrypt is a password-hashing function designed to be computationally intensive, incorporating a salt to protect against rainbow table attacks and allowing adjustable work factor to increase hashing difficulty over time. SHA256 is a cryptographic hash function from the SHA-2 family, producing a fixed 256-bit output commonly used for data integrity verification but not optimized for password hashing due to its fast computation speed. Unlike SHA256, Bcrypt's adaptive nature makes it more resistant to brute-force attacks, making it ideal for securely storing passwords.
Core Differences: Bcrypt vs SHA256
Bcrypt and SHA256 differ fundamentally in their design and security applications, with Bcrypt specifically engineered for password hashing by incorporating a salt and adaptive work factor to resist brute-force attacks. SHA256, a cryptographic hash function, produces a fixed 256-bit hash primarily for data integrity and digital signatures but lacks inherent mechanisms against rainbow table attacks. Bcrypt's computational expense and salting capabilities make it superior for password storage, while SHA256 is optimized for speed and collision resistance in general-purpose hashing.
How Bcrypt Works: Technical Overview
Bcrypt uses the Blowfish cipher to incorporate a salt and adaptive hash function, enhancing security against brute-force attacks by increasing computational cost over time. It generates a unique 128-bit salt and employs key stretching through multiple rounds (configurable cost factor) to slow down hashing processes, making it resistant to hardware-accelerated attacks. This design ensures hashed passwords remain secure even as computing power advances, contrasting with SHA256's fixed iteration approach.
How SHA256 Works: Technical Overview
SHA256 operates by processing input data in 512-bit blocks through a series of 64 compression rounds, utilizing functions like bitwise logical operations, modular additions, and fixed constants derived from the fractional parts of cube roots of prime numbers. The algorithm produces a fixed 256-bit hash output that uniquely represents the input data, ensuring collision resistance and preimage resistance under cryptographic standards. Its core design focuses on speed and deterministic output, making it suitable for integrity verification rather than password hashing, which requires computational cost to deter brute-force attacks.
Security Strength: Bcrypt vs SHA256
Bcrypt offers superior security strength compared to SHA256 due to its adaptive hashing algorithm, which includes built-in salting and a configurable work factor that slows down brute-force attacks. SHA256, while fast and efficient for data integrity, lacks key features like salting and iteration, making it more vulnerable to rainbow table and brute-force attacks when used for password hashing. The computational intensity of Bcrypt significantly enhances resistance against modern GPU-based cracking methods, ensuring stronger protection for sensitive credentials.
Performance and Efficiency Comparison
Bcrypt offers superior security by incorporating a computationally intensive key stretching technique, making it slower but more resilient against brute-force attacks compared to SHA256. While SHA256 processes hashes rapidly due to its design for speed and general-purpose hashing, this efficiency compromises its suitability for password hashing where resistance to attacks is critical. In performance-sensitive applications requiring high security, Bcrypt balances processing time with enhanced protection, whereas SHA256 prioritizes fast computation at the cost of vulnerability to modern attack methods.
Password Hashing: Why Bcrypt Outshines SHA256
Bcrypt outshines SHA256 for password hashing due to its adaptive complexity, which allows it to remain resilient against brute-force attacks as computational power increases. Unlike SHA256, Bcrypt incorporates a built-in salt and a configurable work factor that slows hashing processes, significantly enhancing security by making large-scale hash cracking impractical. This design makes Bcrypt the preferred choice for protecting passwords in modern authentication systems.
Real-World Use Cases for Bcrypt and SHA256
Bcrypt is widely used for securely hashing passwords due to its adaptive work factor that slows down brute-force attacks, making it ideal for authentication systems in web applications. SHA256 is commonly employed for data integrity verification and digital signatures, ensuring files or messages remain unaltered during transmission in blockchain and SSL/TLS protocols. While SHA256 excels in fast, deterministic hashing, Bcrypt is preferred where computational difficulty and resistance to brute-force attacks on passwords are critical.
Common Vulnerabilities and Mitigation
Bcrypt offers stronger resistance against brute-force attacks compared to SHA256 due to its adaptive hash function that increases computational complexity over time. While SHA256 is vulnerable to fast brute-force attacks and rainbow table exploits, bcrypt incorporates salt and multiple iterations to mitigate these risks effectively. Employing bcrypt in password hashing ensures enhanced protection against common vulnerabilities like hash cracking and collision attacks.
Choosing the Right Hashing Algorithm for Your Project
Choosing the right hashing algorithm hinges on the security requirements and performance constraints of your project. Bcrypt offers robust protection against brute-force attacks through adaptive hashing and salting, making it ideal for password storage. SHA256 excels in speed and is suitable for data integrity verification but lacks built-in resistance to brute-force attacks, thus less appropriate for sensitive credential hashing.
Bcrypt vs SHA256 Infographic
 difterm.com
difterm.com