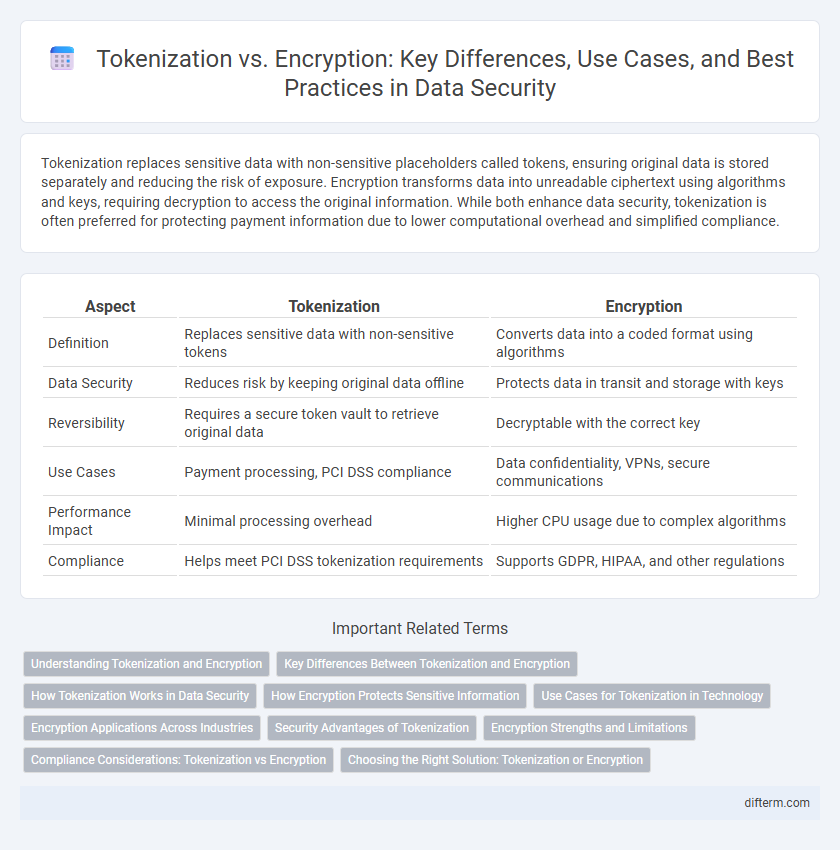
Tokenization replaces sensitive data with non-sensitive placeholders called tokens, ensuring original data is stored separately and reducing the risk of exposure. Encryption transforms data into unreadable ciphertext using algorithms and keys, requiring decryption to access the original information. While both enhance data security, tokenization is often preferred for protecting payment information due to lower computational overhead and simplified compliance.
Table of Comparison
| Aspect | Tokenization | Encryption |
|---|---|---|
| Definition | Replaces sensitive data with non-sensitive tokens | Converts data into a coded format using algorithms |
| Data Security | Reduces risk by keeping original data offline | Protects data in transit and storage with keys |
| Reversibility | Requires a secure token vault to retrieve original data | Decryptable with the correct key |
| Use Cases | Payment processing, PCI DSS compliance | Data confidentiality, VPNs, secure communications |
| Performance Impact | Minimal processing overhead | Higher CPU usage due to complex algorithms |
| Compliance | Helps meet PCI DSS tokenization requirements | Supports GDPR, HIPAA, and other regulations |
Understanding Tokenization and Encryption
Tokenization replaces sensitive data with non-sensitive placeholders called tokens, preserving data format while eliminating exposure risks. Encryption converts data into unreadable ciphertext using algorithms and keys, requiring decryption for access. Understanding the operational differences helps organizations choose appropriate security measures for protecting payment card information and personal data.
Key Differences Between Tokenization and Encryption
Tokenization replaces sensitive data with non-sensitive tokens that have no meaningful value outside a specific system, enhancing data privacy by eliminating the storage of actual data. Encryption transforms data into a coded format using algorithms and keys, allowing it to be securely reversed to its original form through decryption. Key differences include tokenization's irreversibility and system-specific tokens versus encryption's reliance on cryptographic keys enabling data recovery, impacting use cases in data security and compliance.
How Tokenization Works in Data Security
Tokenization in data security replaces sensitive information with unique identification symbols or tokens that retain essential data without compromising its security. These tokens are stored separately from the original data in secure token vaults, minimizing the risk of exposure during data processing or transmission. Unlike encryption, tokenization does not involve complex algorithms for data transformation, making it highly effective for protecting payment card information and complying with industry standards like PCI DSS.
How Encryption Protects Sensitive Information
Encryption secures sensitive information by converting data into an unreadable format using algorithms and cryptographic keys, ensuring that only authorized parties with the correct decryption key can access the original content. This process protects data during transmission and storage, mitigating risks of interception and unauthorized disclosure. Advanced encryption standards (AES) and public-key cryptography are widely implemented to maintain data confidentiality and integrity across various technology platforms.
Use Cases for Tokenization in Technology
Tokenization is widely used in technology to secure sensitive data by substituting it with non-sensitive tokens, enhancing data privacy in payment processing, healthcare records, and cloud computing environments. Unlike encryption, tokenization reduces the risk of data breaches by ensuring that original data never resides in the system, which is critical for compliance with regulations such as PCI DSS and HIPAA. In software development and API integration, tokenization streamlines secure data handling without the computational overhead associated with encryption and decryption processes.
Encryption Applications Across Industries
Encryption is widely implemented across industries such as finance, healthcare, and telecommunications to protect sensitive data from unauthorized access. Financial institutions use encryption to secure online transactions, healthcare providers encrypt patient records to comply with HIPAA regulations, and telecommunications companies safeguard communication channels against interception. This technology ensures data confidentiality, integrity, and compliance with regulatory standards in diverse sectors.
Security Advantages of Tokenization
Tokenization enhances data security by replacing sensitive information with unique tokens that have no exploitable value outside the specific system, reducing the risk of data breaches. Unlike encryption, tokens cannot be reversed or decoded without access to the token vault, minimizing exposure of original data. This approach limits the scope of compliance requirements such as PCI DSS, as sensitive information is not stored within critical systems.
Encryption Strengths and Limitations
Encryption provides robust data protection by converting information into unreadable ciphertext using algorithms such as AES-256, which ensures confidentiality and integrity against unauthorized access. Its strengths include strong security, compliance with regulatory standards like GDPR and HIPAA, and versatility across various data types and transmission channels. Limitations involve potential performance overhead, key management complexities, and vulnerability to attacks if encryption keys are compromised or poorly implemented.
Compliance Considerations: Tokenization vs Encryption
Tokenization reduces compliance scope by replacing sensitive data with non-sensitive substitutes, minimizing exposure under regulations like PCI DSS. Encryption secures data using algorithms but requires key management and comprehensive controls to meet standards such as HIPAA and GDPR. Organizations often prefer tokenization for payment data due to reduced audit requirements and lower risk of data breaches.
Choosing the Right Solution: Tokenization or Encryption
Tokenization replaces sensitive data with non-sensitive equivalents called tokens, reducing exposure during data breaches, while encryption transforms data into unreadable ciphertext requiring keys for access. Choosing the right solution depends on compliance requirements, data usage patterns, and performance needs; tokenization is ideal for minimizing data exposure in payment systems, whereas encryption provides robust protection for data at rest and in transit. Organizations must assess scalability, implementation complexity, and regulatory mandates such as PCI DSS to determine the optimal approach for securing sensitive information.
Tokenization vs Encryption Infographic
 difterm.com
difterm.com