VPNs create secure tunnels for remote access by encrypting data between users and networks, but they often grant broad network access once connected. Zero Trust Network Architecture limits access by verifying every user and device continuously, enforcing least-privilege principles irrespective of location. This approach enhances security against insider threats and lateral movement by segmenting network resources and minimizing trust assumptions.
Table of Comparison
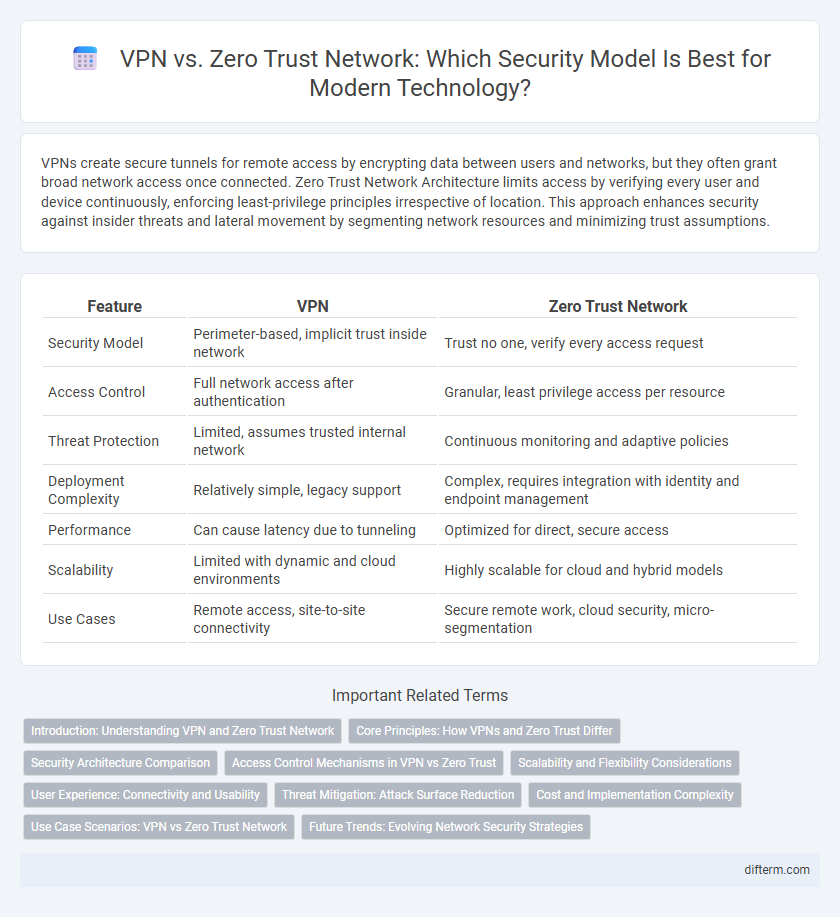
| Feature | VPN | Zero Trust Network |
|---|---|---|
| Security Model | Perimeter-based, implicit trust inside network | Trust no one, verify every access request |
| Access Control | Full network access after authentication | Granular, least privilege access per resource |
| Threat Protection | Limited, assumes trusted internal network | Continuous monitoring and adaptive policies |
| Deployment Complexity | Relatively simple, legacy support | Complex, requires integration with identity and endpoint management |
| Performance | Can cause latency due to tunneling | Optimized for direct, secure access |
| Scalability | Limited with dynamic and cloud environments | Highly scalable for cloud and hybrid models |
| Use Cases | Remote access, site-to-site connectivity | Secure remote work, cloud security, micro-segmentation |
Introduction: Understanding VPN and Zero Trust Network
VPNs create secure tunnels by encrypting data between users and networks, enabling remote access with traditional perimeter-based security models. Zero Trust Networks eliminate implicit trust by continuously verifying every device and user, enforcing strict access controls regardless of location. This shift from perimeter defense to identity-centric security fundamentally changes how organizations protect sensitive data in modern technology environments.
Core Principles: How VPNs and Zero Trust Differ
VPNs create secure tunnels by authenticating users and encrypting data between devices and a trusted network perimeter, relying on implicit trust once inside the network. Zero Trust Networks operate on the principle of "never trust, always verify," enforcing strict identity verification and least-privilege access continuously for every user and device, regardless of location. This fundamental difference ensures Zero Trust provides more granular security controls and reduces the risk of lateral movement within the network compared to traditional VPNs.
Security Architecture Comparison
VPNs create encrypted tunnels to secure remote access but inherently trust users once inside the network perimeter, increasing risk of lateral movement by malicious actors. Zero Trust Network Architecture (ZTNA) enforces strict identity verification and continuous validation for every device and user, minimizing the attack surface through micro-segmentation and least-privilege access. Compared to VPNs, ZTNA offers enhanced protection against insider threats and unauthorized access by eliminating implicit trust assumptions in security design.
Access Control Mechanisms in VPN vs Zero Trust
VPNs rely on perimeter-based access control, granting users broad network access once authenticated, which can increase the attack surface. Zero Trust Networks implement granular access control by continuously verifying user identity and device posture, limiting access to specific resources based on strict policies. This dynamic, context-aware approach enhances security by minimizing lateral movement and ensuring least-privilege access.
Scalability and Flexibility Considerations
Zero Trust Network Architecture (ZTNA) offers superior scalability by enabling granular access controls that adapt dynamically to user behavior and device posture, while traditional VPNs often struggle with fixed perimeter models that limit flexibility. ZTNA's cloud-native design supports seamless integration with diverse environments and rapid scaling to accommodate growing or shifting workloads without compromising security. In contrast, VPNs typically require manual configuration for scaling and often face bottlenecks as the number of users and endpoints increases, reducing overall network agility and responsiveness.
User Experience: Connectivity and Usability
VPNs often create latency and complex login processes that hinder seamless connectivity, impacting user experience negatively. Zero Trust Network architectures prioritize continuous verification and granular access controls, enabling smoother and more secure user interactions without compromising speed. Enhanced usability in Zero Trust environments supports adaptive authentication methods, reducing friction while maintaining robust security.
Threat Mitigation: Attack Surface Reduction
VPNs primarily secure remote access but can inadvertently expand the attack surface by granting broad network access once authenticated. Zero Trust Network Architecture minimizes threat exposure through granular access controls and continuous verification, restricting user permissions strictly to necessary resources. This approach significantly reduces the potential for lateral movement and limits attack vectors compared to traditional VPN models.
Cost and Implementation Complexity
VPNs typically offer lower upfront costs but can incur hidden expenses related to ongoing maintenance and scaling, whereas Zero Trust Network architectures demand higher initial investment due to advanced technology and continuous authentication requirements. Implementation complexity is significantly greater for Zero Trust, involving intricate policy configurations and integration with multiple identity providers, contrasting with VPNs that rely on simpler remote access protocols. Organizations prioritizing cost-efficiency and straightforward deployment may prefer VPNs, while those emphasizing robust security and granular access controls often invest in Zero Trust despite the complexity.
Use Case Scenarios: VPN vs Zero Trust Network
VPNs are effective for remote access to internal corporate networks, enabling employees to securely connect from any location by extending the network perimeter. Zero Trust Network Architecture (ZTNA) applies granular access controls based on user identity, device health, and location, ideal for dynamic cloud environments and minimizing lateral movement risks. Organizations managing hybrid workforces and multi-cloud infrastructures benefit from ZTNA's continuous verification over VPN's broad trust model.
Future Trends: Evolving Network Security Strategies
VPNs have long been a staple in remote access security, yet zero trust networks are rapidly redefining cybersecurity paradigms by enforcing strict identity verification and least-privilege access. Future trends indicate a shift towards zero trust architectures integrating AI-driven threat detection and micro-segmentation to minimize attack surfaces. This evolution reflects the increasing complexity of cyber threats and the need for adaptive, context-aware network security strategies.
VPN vs Zero Trust Network Infographic
 difterm.com
difterm.com