Hashing transforms data into a fixed-size string of characters, typically used for verifying data integrity, while encryption converts data into a coded format that can be reversed with a key to ensure confidentiality. Hashing is a one-way process, making it ideal for password storage, whereas encryption is two-way, enabling secure communication by allowing data to be decrypted. Both hashing and encryption play crucial roles in securing technology applications, with hashing focused on authentication and encryption on privacy.
Table of Comparison
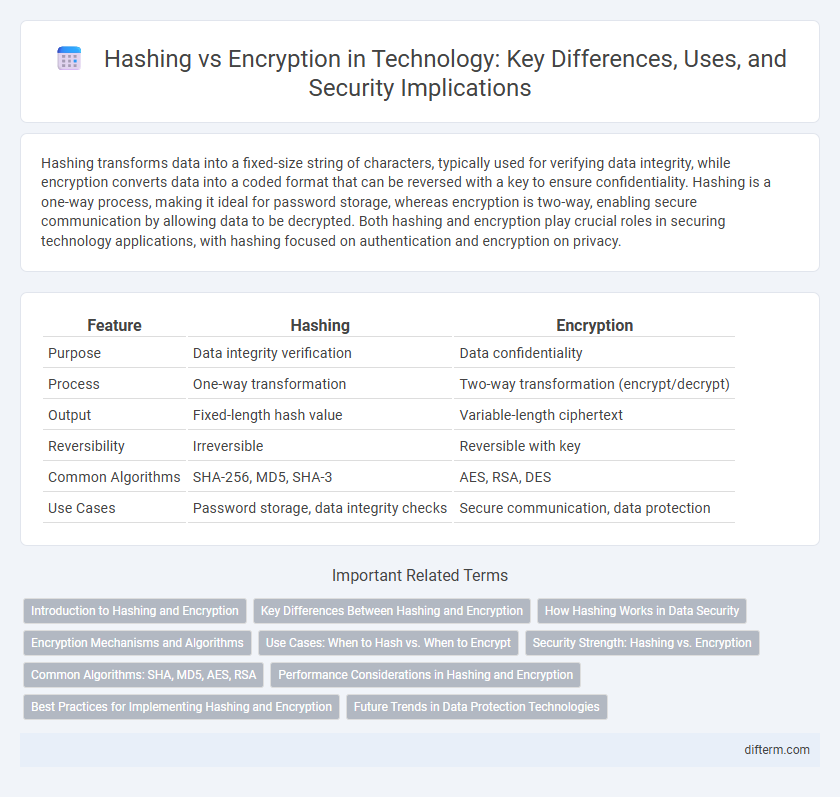
| Feature | Hashing | Encryption |
|---|---|---|
| Purpose | Data integrity verification | Data confidentiality |
| Process | One-way transformation | Two-way transformation (encrypt/decrypt) |
| Output | Fixed-length hash value | Variable-length ciphertext |
| Reversibility | Irreversible | Reversible with key |
| Common Algorithms | SHA-256, MD5, SHA-3 | AES, RSA, DES |
| Use Cases | Password storage, data integrity checks | Secure communication, data protection |
Introduction to Hashing and Encryption
Hashing transforms input data into a fixed-size string of characters, typically used for data integrity verification and password storage, whereas encryption converts data into an unreadable format to ensure confidentiality, allowing only authorized parties to decrypt it. Hashing algorithms, such as SHA-256 and MD5, produce unique hash values but cannot be reversed to retrieve original data, while encryption algorithms, including AES and RSA, use keys for reversible data protection. Understanding the fundamental differences between hashing and encryption is essential for implementing secure authentication, data protection, and cryptographic protocols in modern technology systems.
Key Differences Between Hashing and Encryption
Hashing generates a fixed-length hash value from input data, designed for integrity verification and is one-way, making it impossible to retrieve the original data from the hash. Encryption transforms data into ciphertext using algorithms and keys, allowing authorized parties to decrypt and access the original information. The primary difference lies in hashing's irreversible process for data validation versus encryption's reversible process focused on confidentiality and secure communication.
How Hashing Works in Data Security
Hashing transforms input data into a fixed-size string of characters, representing the original data uniquely through complex mathematical algorithms such as SHA-256 or MD5. This one-way process ensures data integrity by generating a distinct hash value, making it nearly impossible to reverse-engineer the original content or produce identical hashes with different inputs. Hash functions are crucial in password storage, digital signatures, and blockchain technology, providing a reliable method for verifying data authenticity without exposing sensitive information.
Encryption Mechanisms and Algorithms
Encryption mechanisms rely on algorithms such as AES, RSA, and ECC to securely transform plaintext into ciphertext, ensuring data confidentiality and integrity. Symmetric encryption algorithms like AES use a single key for both encryption and decryption, making them efficient for large data volumes. Asymmetric encryption algorithms, including RSA and ECC, use distinct public and private keys, providing robust security for key exchange and digital signatures in communication protocols.
Use Cases: When to Hash vs. When to Encrypt
Hashing is ideal for verifying data integrity and storing passwords securely, as it produces a fixed-size output and is irreversible. Encryption is best suited for protecting sensitive information during transmission or storage, allowing data to be restored to its original form with the correct decryption key. Choosing between hashing and encryption depends on whether data needs to be verified without retrieval or securely accessed and recovered later.
Security Strength: Hashing vs. Encryption
Hashing provides strong security by generating fixed-size, unique digests from data, making it nearly impossible to reverse-engineer the original input. Encryption secures data by transforming it into ciphertext using keys, allowing safe two-way data access only for authorized parties with the correct decryption keys. While hashing ensures data integrity and verification, encryption offers robust confidentiality by protecting sensitive information from unauthorized access.
Common Algorithms: SHA, MD5, AES, RSA
SHA and MD5 are widely used hashing algorithms designed to produce fixed-size, unique digests for data integrity verification, with SHA providing stronger security compared to the deprecated MD5. AES and RSA serve as encryption algorithms, where AES uses symmetric key cryptography for fast and secure data encryption, and RSA relies on asymmetric key encryption enabling secure key exchange and digital signatures. Understanding the distinct purposes and strengths of hashing versus encryption algorithms is critical for implementing effective data security solutions.
Performance Considerations in Hashing and Encryption
Hashing algorithms generally offer faster performance than encryption methods due to their one-way computation process, which requires less computational overhead. Encryption involves transforming data into a reversible format using cryptographic keys, often demanding more processing power and time, especially with complex algorithms like AES or RSA. Performance efficiency in hashing makes it ideal for integrity verification and quick data indexing, whereas encryption prioritizes data confidentiality over speed.
Best Practices for Implementing Hashing and Encryption
Best practices for implementing hashing involve using strong, cryptographically secure hash functions such as SHA-256 or bcrypt, combined with salting to protect against rainbow table attacks. Encryption should employ advanced algorithms like AES-256 with proper key management and regular key rotation to maintain data confidentiality. Ensuring the use of well-vetted cryptographic libraries and integrating multi-factor authentication strengthens the overall security posture.
Future Trends in Data Protection Technologies
Future trends in data protection emphasize advanced hashing algorithms paired with quantum-resistant encryption methods to enhance security against evolving cyber threats. Innovations like homomorphic encryption and blockchain-integrated hashing enable secure data processing and verification without exposing sensitive information. Embracing AI-driven anomaly detection further strengthens encryption and hashing mechanisms by proactively identifying vulnerabilities in real time.
hashing vs encryption Infographic
 difterm.com
difterm.com