Spoofing and phishing are common cybersecurity threats targeting pet technology devices, where spoofing involves falsifying device identities to gain unauthorized access, while phishing tricks users into revealing sensitive information through deceptive messages. Both techniques compromise the security and privacy of smart pet products, such as GPS trackers and automated feeders, making it essential to implement robust authentication measures. Understanding these threats helps pet owners protect their devices from cyber attacks and ensure the safety of their pets.
Table of Comparison
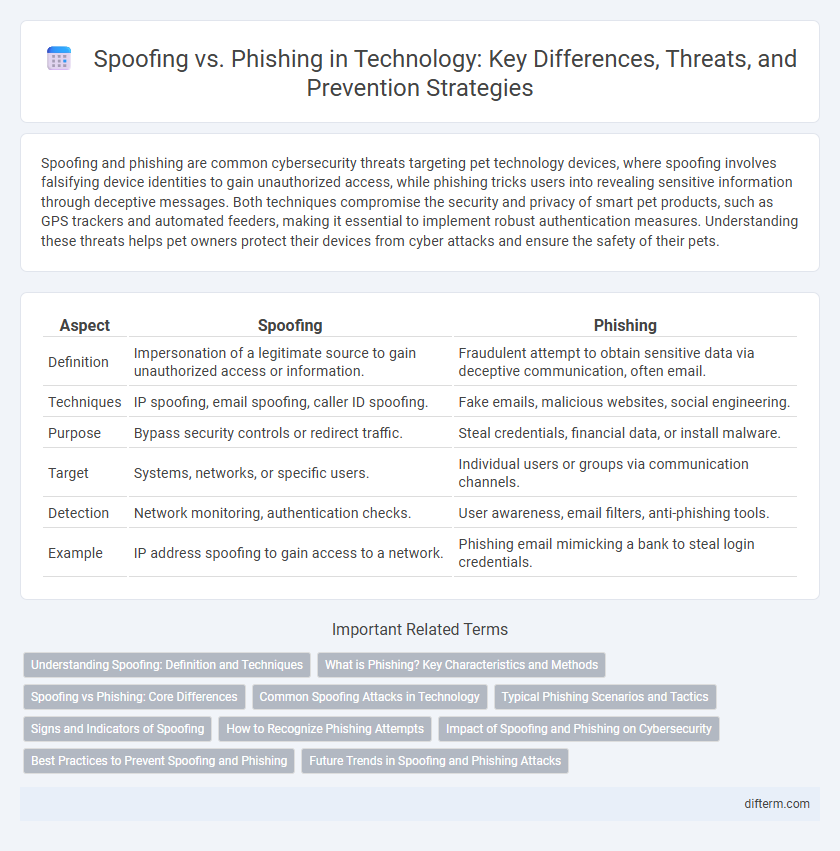
| Aspect | Spoofing | Phishing |
|---|---|---|
| Definition | Impersonation of a legitimate source to gain unauthorized access or information. | Fraudulent attempt to obtain sensitive data via deceptive communication, often email. |
| Techniques | IP spoofing, email spoofing, caller ID spoofing. | Fake emails, malicious websites, social engineering. |
| Purpose | Bypass security controls or redirect traffic. | Steal credentials, financial data, or install malware. |
| Target | Systems, networks, or specific users. | Individual users or groups via communication channels. |
| Detection | Network monitoring, authentication checks. | User awareness, email filters, anti-phishing tools. |
| Example | IP address spoofing to gain access to a network. | Phishing email mimicking a bank to steal login credentials. |
Understanding Spoofing: Definition and Techniques
Spoofing involves creating a deceptive appearance by falsifying data to gain unauthorized access or steal information, commonly using techniques like IP spoofing, email spoofing, and caller ID spoofing. Attackers manipulate sender addresses or device identifiers to impersonate trusted entities, tricking users or security systems into granting access or divulging sensitive data. Understanding these methods is crucial for developing robust cybersecurity defenses and recognizing spoofing attempts in digital communications.
What is Phishing? Key Characteristics and Methods
Phishing is a cyberattack technique that involves tricking individuals into revealing sensitive information such as passwords, credit card numbers, or personal data by masquerading as a trustworthy entity through emails, fake websites, or messages. Key characteristics of phishing include deceptive communication, urgency or fear tactics, and links to fraudulent websites designed to steal credentials. Common phishing methods involve spear phishing, where attackers target specific individuals, and clone phishing, which replicates legitimate communications to deceive recipients.
Spoofing vs Phishing: Core Differences
Spoofing involves impersonating a trusted entity by falsifying data such as IP addresses, emails, or websites to gain unauthorized access or spread malware, whereas phishing specifically targets individuals through deceptive emails or messages to steal sensitive information like passwords or credit card details. Spoofing can be a broader attack method used within phishing campaigns to enhance credibility, making phishing a subset of social engineering attacks often relying on spoofed communications. Understanding these core differences is crucial for implementing effective cybersecurity measures, including email authentication protocols like SPF, DKIM, and DMARC to combat spoofing and user awareness training to prevent phishing.
Common Spoofing Attacks in Technology
Common spoofing attacks in technology include email spoofing, where attackers impersonate trusted senders to deliver malicious messages, and IP spoofing, which masks the origin of network traffic to bypass security measures. DNS spoofing manipulates domain name system records to redirect users to fraudulent websites, while caller ID spoofing misleads recipients by displaying false phone numbers. These attacks exploit trust mechanisms in communication protocols, posing significant risks to cybersecurity.
Typical Phishing Scenarios and Tactics
Typical phishing scenarios involve deceptive emails or websites that mimic legitimate organizations to steal sensitive information such as login credentials or financial details. Attackers often use tactics like creating urgent messages, fake login prompts, or malicious attachments to trick victims into revealing personal data. Social engineering techniques, including impersonation and spear phishing, enhance the effectiveness of these fraudulent schemes by targeting specific individuals or organizations.
Signs and Indicators of Spoofing
Spoofing often involves fake IP addresses, email addresses, or websites designed to mimic legitimate ones, making technical indicators such as mismatched URLs, unusual sender email domains, or inconsistencies in SSL certificates crucial signs. Users should watch for unexpected requests for sensitive information, time-stamped irregularities in email headers, and discrepancies in digital signatures that typically indicate a spoofing attempt. Recognizing these signs helps in differentiating spoofing from phishing, as spoofing primarily exploits technical manipulations rather than purely deceptive content.
How to Recognize Phishing Attempts
Phishing attempts can be recognized by scrutinizing suspicious email addresses, unexpected requests for personal information, and urgent language designed to provoke immediate action. Hovering over links to verify URLs before clicking helps identify deceptive redirects commonly used in phishing. Unsolicited messages that contain grammatical errors or lack personalization often signal phishing rather than legitimate spoofing attacks.
Impact of Spoofing and Phishing on Cybersecurity
Spoofing and phishing significantly undermine cybersecurity by enabling attackers to impersonate legitimate entities and deceive users into divulging sensitive information or installing malware. These threats lead to data breaches, financial losses, and erosion of trust in digital systems, affecting individuals, businesses, and critical infrastructure. Effective countermeasures include multi-factor authentication, email filtering, and continuous user education to mitigate the impact on security frameworks.
Best Practices to Prevent Spoofing and Phishing
Implement strong email authentication protocols such as SPF, DKIM, and DMARC to effectively prevent spoofing attacks. Educate employees and users to recognize phishing indicators like suspicious links, unexpected attachments, and request for sensitive information. Regularly update software and security systems while conducting phishing simulation training to enhance organizational resilience.
Future Trends in Spoofing and Phishing Attacks
Future trends in spoofing and phishing attacks include the increasing use of artificial intelligence and machine learning to create more sophisticated and harder-to-detect scams. Attackers are expected to exploit deepfake technology and advanced social engineering techniques to enhance the realism of their fraudulent communications. Emerging defenses will leverage behavioral analytics and AI-driven threat detection to counter these evolving cyber threats.
Spoofing vs Phishing Infographic
 difterm.com
difterm.com