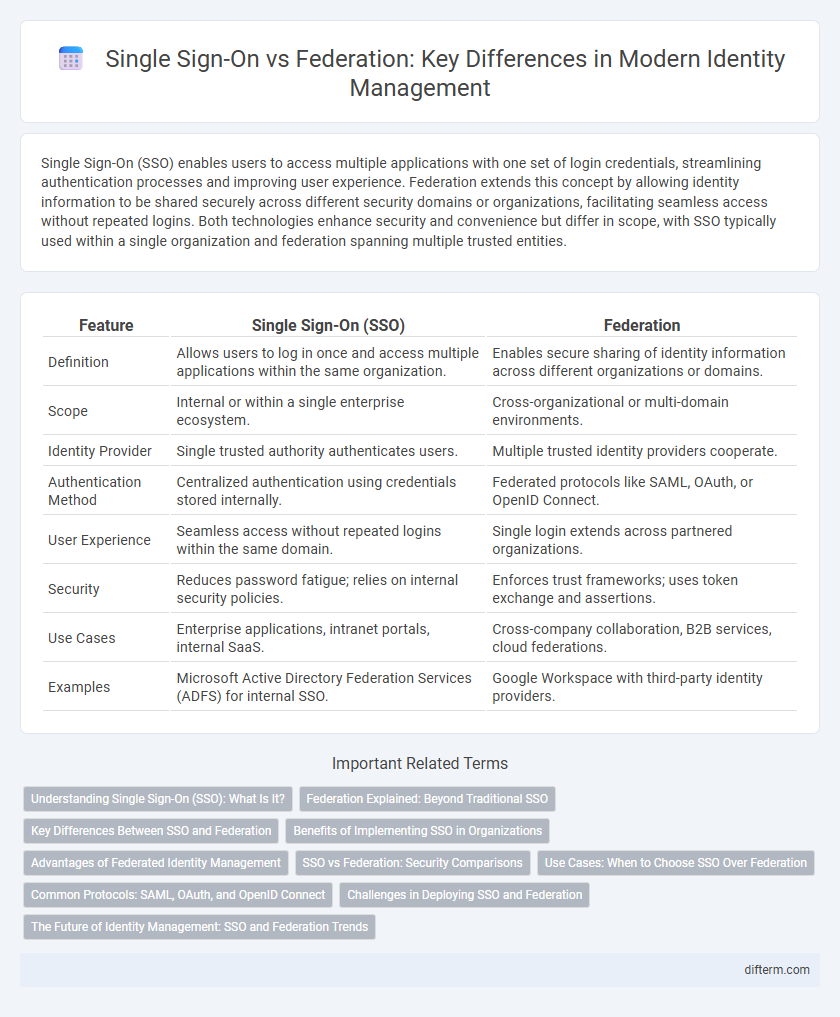
Single Sign-On (SSO) enables users to access multiple applications with one set of login credentials, streamlining authentication processes and improving user experience. Federation extends this concept by allowing identity information to be shared securely across different security domains or organizations, facilitating seamless access without repeated logins. Both technologies enhance security and convenience but differ in scope, with SSO typically used within a single organization and federation spanning multiple trusted entities.
Table of Comparison
| Feature | Single Sign-On (SSO) | Federation |
|---|---|---|
| Definition | Allows users to log in once and access multiple applications within the same organization. | Enables secure sharing of identity information across different organizations or domains. |
| Scope | Internal or within a single enterprise ecosystem. | Cross-organizational or multi-domain environments. |
| Identity Provider | Single trusted authority authenticates users. | Multiple trusted identity providers cooperate. |
| Authentication Method | Centralized authentication using credentials stored internally. | Federated protocols like SAML, OAuth, or OpenID Connect. |
| User Experience | Seamless access without repeated logins within the same domain. | Single login extends across partnered organizations. |
| Security | Reduces password fatigue; relies on internal security policies. | Enforces trust frameworks; uses token exchange and assertions. |
| Use Cases | Enterprise applications, intranet portals, internal SaaS. | Cross-company collaboration, B2B services, cloud federations. |
| Examples | Microsoft Active Directory Federation Services (ADFS) for internal SSO. | Google Workspace with third-party identity providers. |
Understanding Single Sign-On (SSO): What Is It?
Single Sign-On (SSO) is an authentication process that allows users to access multiple applications with one set of credentials, enhancing security and user convenience. It streamlines user experience by eliminating repeated logins, reducing password fatigue, and minimizing the risk of credential theft. SSO systems rely on centralized identity providers and protocols like SAML, OAuth, or OpenID Connect to manage secure authentication across diverse platforms.
Federation Explained: Beyond Traditional SSO
Federation extends beyond traditional Single Sign-On (SSO) by enabling users to access multiple systems across organizational boundaries using a single authentication process. It leverages trust relationships and standards like SAML, OAuth, and OpenID Connect to facilitate seamless identity management and secure resource sharing between disparate domains. Federation enhances user experience and security by allowing decentralized identity providers to authenticate users without requiring multiple credentials.
Key Differences Between SSO and Federation
Single Sign-On (SSO) enables users to access multiple applications with one set of login credentials within a single domain, streamlining authentication and reducing password fatigue. Federation extends this concept across different security domains or organizations, allowing users to use one identity to access resources on external systems through trust relationships and standardized protocols like SAML or OAuth. The primary difference lies in SSO's domain-specific access versus federation's cross-domain identity sharing and trust management.
Benefits of Implementing SSO in Organizations
Single Sign-On (SSO) streamlines user access by allowing employees to authenticate once and gain entry to multiple applications, reducing password fatigue and improving productivity. Implementing SSO enhances security by minimizing credential exposure and facilitating centralized access control, which simplifies compliance with industry regulations like GDPR and HIPAA. Organizations benefit from decreased IT support costs due to fewer password reset requests and faster onboarding processes.
Advantages of Federated Identity Management
Federated Identity Management enhances user experience by enabling seamless access across multiple systems without repeated logins, improving security through centralized credential management and reducing password fatigue. It supports interoperability among diverse organizations and platforms by standardizing authentication protocols such as SAML and OAuth. This framework simplifies IT administration and compliance by consolidating user identities and access policies across federated domains.
SSO vs Federation: Security Comparisons
Single Sign-On (SSO) centralizes authentication, reducing password fatigue but increasing risk if credentials are compromised, whereas Federation distributes authentication across trusted domains, enhancing security by limiting credential exposure. Federation leverages standards like SAML and OAuth to enable secure access across multiple organizations without sharing passwords directly. Both approaches improve user convenience, yet Federation offers stronger security boundaries by isolating authentication sessions and minimizing attack surfaces in multi-organization environments.
Use Cases: When to Choose SSO Over Federation
Single Sign-On (SSO) is ideal for organizations requiring seamless user access across multiple internal applications within a single domain or trusted environment, enhancing user productivity and security. Federation is best suited for scenarios involving cross-domain access where independent identity providers authenticate users, such as partner ecosystems or multi-organization collaborations. Choose SSO over Federation when the primary need is centralized authentication within a controlled enterprise environment to simplify credential management and reduce login fatigue.
Common Protocols: SAML, OAuth, and OpenID Connect
SAML, OAuth, and OpenID Connect are prevalent protocols enabling secure authentication in Single Sign-On (SSO) and federated identity systems. SAML is widely used for enterprise SSO due to its XML-based assertions supporting browser-based authentication, while OAuth provides authorization for API access, granting limited permissions without exposing user credentials. OpenID Connect, built on OAuth 2.0, adds an identity layer for authenticating users across different domains, seamlessly supporting both SSO and federation scenarios.
Challenges in Deploying SSO and Federation
Deploying Single Sign-On (SSO) and Federation presents challenges such as ensuring seamless integration across diverse identity providers and maintaining robust security protocols to prevent unauthorized access. Scalability issues arise when managing multiple applications and user bases, alongside complexities in aligning different authentication standards like SAML, OAuth, and OpenID Connect. Organizations must also address user privacy concerns and compliance with regulations such as GDPR while minimizing downtime during implementation.
The Future of Identity Management: SSO and Federation Trends
Single Sign-On (SSO) and Federation are evolving rapidly to address growing demands for seamless, secure access across multiple platforms and applications. The future of identity management emphasizes decentralized identity models, leveraging blockchain technology to enhance privacy and user control. Trends also include increased adoption of AI-driven authentication and adaptive security measures integrated within SSO and federation frameworks to prevent breaches and simplify user experiences.
Single Sign-On vs Federation Infographic
 difterm.com
difterm.com