Multi-factor authentication (MFA) enhances security by requiring users to verify their identity through multiple independent credentials, such as passwords, biometrics, and security tokens. Two-factor authentication (2FA) is a subset of MFA that specifically involves exactly two verification methods, commonly combining something you know, like a password, with something you have, like a mobile device. MFA provides a broader security framework by incorporating more than two factors, significantly reducing the risk of unauthorized access compared to 2FA.
Table of Comparison
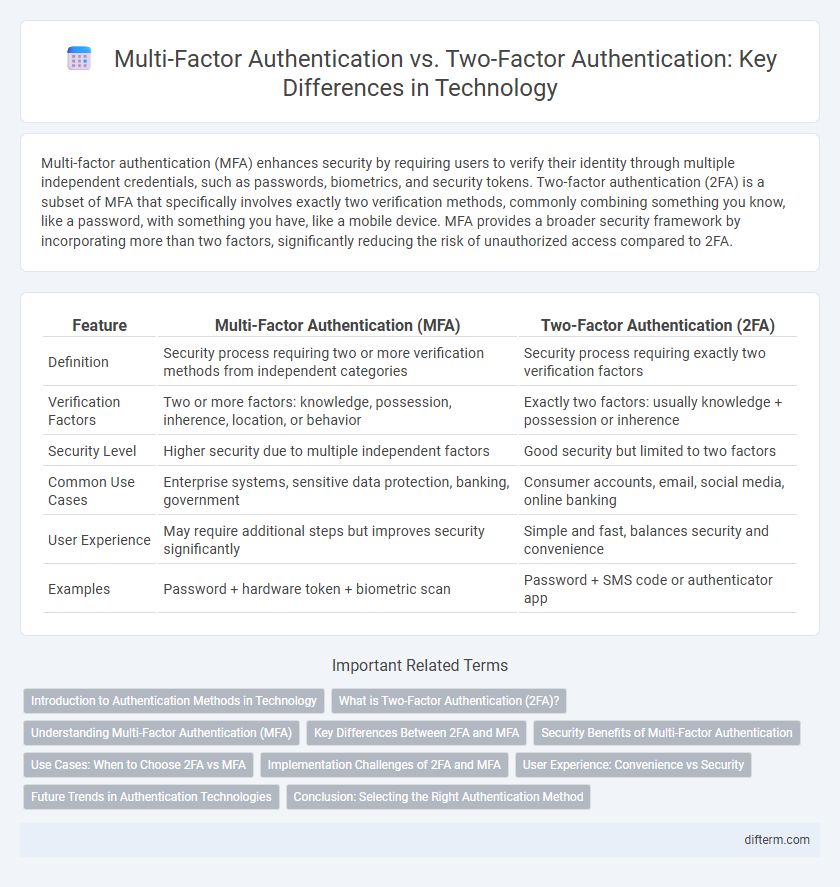
| Feature | Multi-Factor Authentication (MFA) | Two-Factor Authentication (2FA) |
|---|---|---|
| Definition | Security process requiring two or more verification methods from independent categories | Security process requiring exactly two verification factors |
| Verification Factors | Two or more factors: knowledge, possession, inherence, location, or behavior | Exactly two factors: usually knowledge + possession or inherence |
| Security Level | Higher security due to multiple independent factors | Good security but limited to two factors |
| Common Use Cases | Enterprise systems, sensitive data protection, banking, government | Consumer accounts, email, social media, online banking |
| User Experience | May require additional steps but improves security significantly | Simple and fast, balances security and convenience |
| Examples | Password + hardware token + biometric scan | Password + SMS code or authenticator app |
Introduction to Authentication Methods in Technology
Multi-factor authentication (MFA) enhances security by requiring users to verify their identity through two or more independent factors, such as something they know (password), something they have (security token), or something they are (biometric). Two-factor authentication (2FA) is a subset of MFA, involving only two distinct factors, commonly a password combined with a temporary code sent to a mobile device. These authentication methods protect against unauthorized access by adding layers of verification beyond traditional passwords, reducing the risk of breaches in technological systems.
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is a security process requiring users to provide two different types of identification before granting access to an account or system. Typically, this involves something the user knows (like a password) and something they have (such as a smartphone app generating a time-based one-time password). 2FA significantly reduces the risk of unauthorized access by adding an extra verification layer beyond just a password.
Understanding Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) enhances security by requiring users to provide two or more verification factors from different categories: something they know (password), something they have (security token), or something they are (biometric data). Unlike two-factor authentication (2FA), which strictly involves two layers, MFA supports multiple authentication methods, strengthening protection against unauthorized access. Implementing MFA significantly reduces the risk of breaches by ensuring that compromised credentials alone are insufficient for system entry.
Key Differences Between 2FA and MFA
Two-factor authentication (2FA) requires exactly two independent credentials for user identity verification, typically combining something you know (password) with something you have (a mobile device). Multi-factor authentication (MFA) expands this concept by incorporating two or more verification factors, possibly including biometric data like fingerprints or facial recognition, enhancing security layers beyond 2FA. The key difference lies in MFA's flexibility to use multiple types of authentication factors, significantly reducing the risk of unauthorized access compared to the more limited 2FA.
Security Benefits of Multi-Factor Authentication
Multi-factor authentication (MFA) enhances security by requiring users to provide two or more verification factors, significantly reducing the risk of unauthorized access compared to two-factor authentication (2FA) which relies on only two factors. MFA incorporates diverse authentication methods such as biometrics, hardware tokens, and behavioral analysis, offering stronger defense against phishing, password breaches, and identity theft. Implementing multi-factor authentication ensures comprehensive protection for sensitive data and compliance with stringent cybersecurity regulations.
Use Cases: When to Choose 2FA vs MFA
Two-factor authentication (2FA) is ideal for personal accounts and low-risk environments where a simple secondary layer, such as a text message code or an authenticator app, suffices to prevent unauthorized access. Multi-factor authentication (MFA) is essential in enterprise settings, financial services, healthcare, and other high-security areas requiring multiple verification methods like biometrics, hardware tokens, and one-time passwords for enhanced protection against sophisticated cyber threats. Organizations should evaluate the sensitivity of their data and regulatory compliance requirements to determine whether 2FA or MFA best balances security needs and user convenience.
Implementation Challenges of 2FA and MFA
Implementing two-factor authentication (2FA) often faces challenges such as user resistance due to added steps and compatibility issues with legacy systems. Multi-factor authentication (MFA) complicates deployment further by requiring the integration of diverse verification methods like biometrics, tokens, and behavioral analysis, which can increase costs and technical complexity. Both approaches demand robust user education and seamless system interoperability to ensure security without compromising usability.
User Experience: Convenience vs Security
Multi-factor authentication (MFA) enhances security by requiring users to verify identity through multiple layers such as biometrics, security tokens, and passwords, offering a robust defense against unauthorized access. Two-factor authentication (2FA), a subset of MFA, typically combines two methods like a password and a one-time code, balancing ease of use with improved security. While 2FA provides a simpler and faster user experience, MFA often introduces added complexity but significantly reduces risk, making the choice dependent on the required security level and user convenience preferences.
Future Trends in Authentication Technologies
Multi-factor authentication (MFA) is evolving beyond traditional two-factor authentication (2FA) by integrating biometric verification, behavioral analytics, and AI-driven risk assessment to enhance security. Future trends emphasize adaptive authentication methods that dynamically adjust security requirements based on user context and threat intelligence. These advancements aim to reduce friction while providing robust protection against increasingly sophisticated cyberattacks.
Conclusion: Selecting the Right Authentication Method
Multi-factor authentication (MFA) provides stronger security by requiring two or more verification methods, reducing the risk of unauthorized access compared to two-factor authentication (2FA), which uses exactly two factors. Organizations should assess their security needs, user convenience, and regulatory requirements to determine the most suitable approach. Deploying MFA often enhances protection for sensitive data and critical systems, making it the preferred choice for high-security environments.
Multi-factor authentication vs Two-factor authentication Infographic
 difterm.com
difterm.com