Zero trust security eliminates the assumption of trust within a network, requiring continuous verification of user identity and device integrity before granting access. Perimeter security relies on a defined boundary, protecting the network from external threats but often leaving internal vulnerabilities unchecked. Adopting zero trust enhances protection against sophisticated cyberattacks by minimizing potential attack surfaces beyond traditional perimeter defenses.
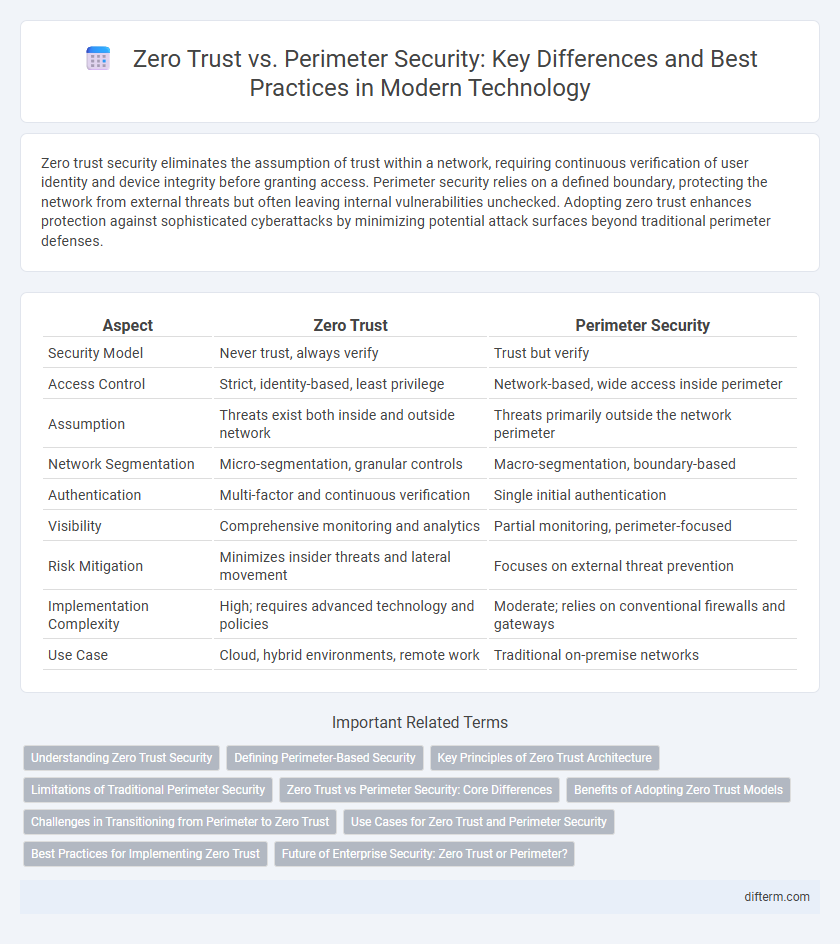
Table of Comparison
| Aspect | Zero Trust | Perimeter Security |
|---|---|---|
| Security Model | Never trust, always verify | Trust but verify |
| Access Control | Strict, identity-based, least privilege | Network-based, wide access inside perimeter |
| Assumption | Threats exist both inside and outside network | Threats primarily outside the network perimeter |
| Network Segmentation | Micro-segmentation, granular controls | Macro-segmentation, boundary-based |
| Authentication | Multi-factor and continuous verification | Single initial authentication |
| Visibility | Comprehensive monitoring and analytics | Partial monitoring, perimeter-focused |
| Risk Mitigation | Minimizes insider threats and lateral movement | Focuses on external threat prevention |
| Implementation Complexity | High; requires advanced technology and policies | Moderate; relies on conventional firewalls and gateways |
| Use Case | Cloud, hybrid environments, remote work | Traditional on-premise networks |
Understanding Zero Trust Security
Zero Trust Security eliminates traditional perimeter barriers by continuously verifying every access request regardless of network location, reducing risks posed by insider threats and compromised credentials. Unlike perimeter security, which relies on trusted internal networks, Zero Trust enforces strict identity verification, micro-segmentation, and least-privilege access. This approach leverages multi-factor authentication, continuous monitoring, and adaptive policies to secure modern distributed environments and cloud infrastructures effectively.
Defining Perimeter-Based Security
Perimeter-based security establishes a defined boundary, such as firewalls and VPNs, to control and monitor network access by trusting devices within that boundary. It relies on a fixed network edge to differentiate between trusted internal users and untrusted external threats, assuming that threats come mainly from outside the perimeter. This traditional security model often struggles to protect modern environments involving cloud services, remote work, and mobile devices where network boundaries are blurred.
Key Principles of Zero Trust Architecture
Zero Trust Architecture operates on the foundational principle of "never trust, always verify," requiring continuous authentication and strict access controls regardless of network location. Unlike traditional perimeter security that assumes entities inside the network are trustworthy, zero trust mandates micro-segmentation, least-privilege access, and real-time monitoring to minimize attack surfaces. This approach ensures robust protection against insider threats and lateral movement by enforcing identity verification and device compliance at every access request.
Limitations of Traditional Perimeter Security
Traditional perimeter security relies heavily on defined network boundaries, making it vulnerable to modern threats like insider attacks and sophisticated phishing. It struggles to protect data once attackers breach the perimeter, leading to potential lateral movement within the network. Zero trust architecture addresses these limitations by continuously verifying users and devices regardless of their location, enhancing overall cybersecurity resilience.
Zero Trust vs Perimeter Security: Core Differences
Zero Trust security operates on the principle of "never trust, always verify," requiring continuous authentication and strict access controls regardless of network location, whereas perimeter security focuses on defending a fixed boundary or firewall to prevent unauthorized access. Zero Trust minimizes insider threats and lateral movement by segmenting networks and enforcing least privilege access, contrasting with perimeter security's reliance on a strong outer defense that assumes internal users are trustworthy. Core differences include Zero Trust's emphasis on identity verification and micro-segmentation versus perimeter security's perimeter-based defense strategy, making Zero Trust more effective in modern hybrid and cloud environments.
Benefits of Adopting Zero Trust Models
Zero Trust models enhance cybersecurity by verifying every user and device, reducing the risk of internal and external threats unlike traditional perimeter security that assumes trust within network boundaries. This approach minimizes attack surfaces and limits lateral movement, ensuring sensitive data remains protected even if a breach occurs. Implementing Zero Trust increases visibility and control, enabling swift detection and response to anomalies across all access points.
Challenges in Transitioning from Perimeter to Zero Trust
Transitioning from perimeter security to zero trust architecture presents challenges such as the complexity of integrating existing legacy systems with continuous verification protocols and enforcing strict access controls based on user behavior and device health. Organizations often face difficulties in redesigning network infrastructure to support micro-segmentation and real-time threat detection without impacting performance. Ensuring employee training and adapting security policies to accommodate zero trust principles are critical to overcoming resistance and achieving effective implementation.
Use Cases for Zero Trust and Perimeter Security
Zero Trust architecture excels in securing cloud environments, remote workforces, and mobile users by enforcing strict identity verification and continuous monitoring regardless of network location. Perimeter security remains effective for safeguarding traditional on-premises networks with clear physical or logical boundaries, such as corporate offices or data centers. Use cases for Zero Trust include protecting sensitive data in hybrid clouds, while perimeter security is suited for environments with well-defined network entry points requiring firewall and VPN protections.
Best Practices for Implementing Zero Trust
Implementing Zero Trust requires continuous verification of user identity through multi-factor authentication and strict access controls, minimizing the reliance on traditional perimeter defenses. Micro-segmentation and least-privilege access policies limit lateral movement within networks, enhancing security against internal threats. Continuous monitoring and adaptive policies ensure dynamic response to evolving threats, making Zero Trust a more resilient approach than perimeter security models.
Future of Enterprise Security: Zero Trust or Perimeter?
Zero Trust security frameworks prioritize continuous verification and least privilege access, making them more adaptive to the increasing cloud adoption and remote workforce trends shaping the future of enterprise security. Perimeter security, reliant on traditional network boundaries, faces limitations against modern threats that exploit decentralized environments and mobile devices. Enterprises investing in Zero Trust architectures gain resilience against sophisticated cyberattacks by minimizing implicit trust and enforcing strict identity verification across all access points.
zero trust vs perimeter security Infographic
 difterm.com
difterm.com