Quantum encryption leverages the principles of quantum mechanics to provide ultra-secure communication by detecting any eavesdropping attempts, making it virtually unbreakable. Symmetric encryption relies on a shared secret key for both encryption and decryption, offering faster processing but higher vulnerability if the key is compromised. Quantum encryption enhances security in the pet technology sector by protecting sensitive data from cyber threats that traditional symmetric encryption might not withstand.
Table of Comparison
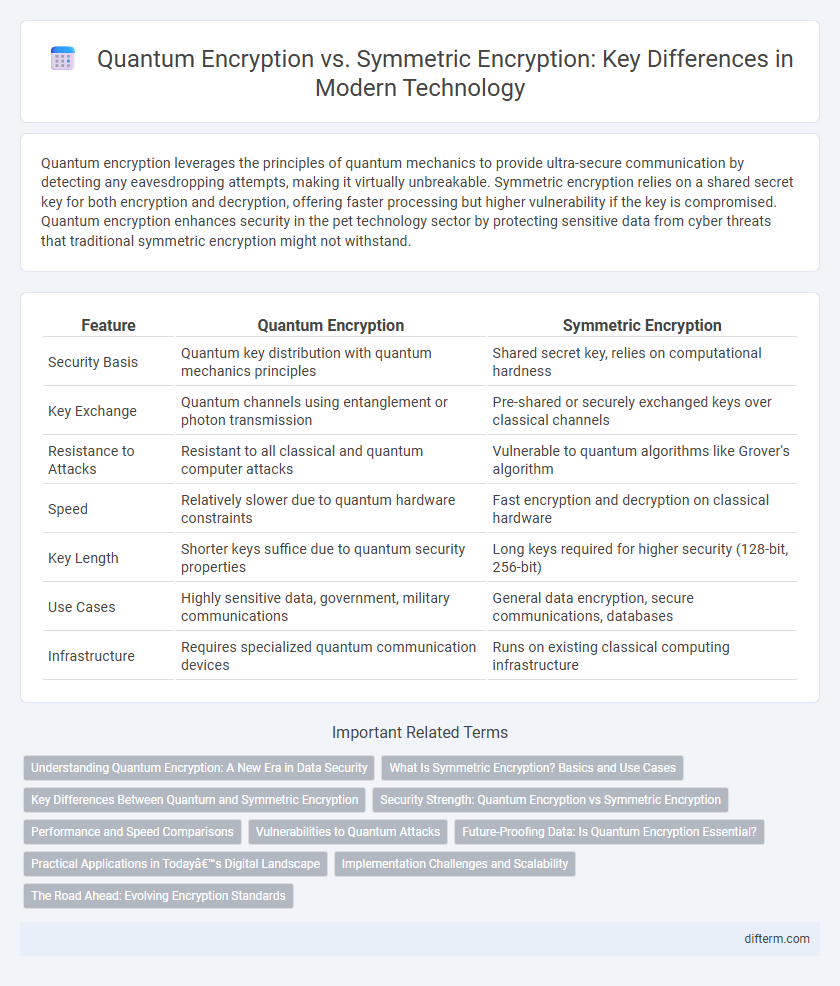
| Feature | Quantum Encryption | Symmetric Encryption |
|---|---|---|
| Security Basis | Quantum key distribution with quantum mechanics principles | Shared secret key, relies on computational hardness |
| Key Exchange | Quantum channels using entanglement or photon transmission | Pre-shared or securely exchanged keys over classical channels |
| Resistance to Attacks | Resistant to all classical and quantum computer attacks | Vulnerable to quantum algorithms like Grover's algorithm |
| Speed | Relatively slower due to quantum hardware constraints | Fast encryption and decryption on classical hardware |
| Key Length | Shorter keys suffice due to quantum security properties | Long keys required for higher security (128-bit, 256-bit) |
| Use Cases | Highly sensitive data, government, military communications | General data encryption, secure communications, databases |
| Infrastructure | Requires specialized quantum communication devices | Runs on existing classical computing infrastructure |
Understanding Quantum Encryption: A New Era in Data Security
Quantum encryption leverages principles of quantum mechanics, such as superposition and entanglement, to create theoretically unbreakable encryption keys through quantum key distribution (QKD). Unlike symmetric encryption, which relies on shared secret keys vulnerable to computational attacks, quantum encryption enables secure key exchange that detects eavesdropping in real-time. This breakthrough positions quantum encryption as a transformative advancement in data security, capable of safeguarding information against future quantum computer threats.
What Is Symmetric Encryption? Basics and Use Cases
Symmetric encryption uses a single key for both encrypting and decrypting data, making it efficient for securing large volumes of information quickly. Common algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard), widely applied in data storage, secure communications, and VPNs. Its simplicity and speed suit environments where key distribution can be securely managed, contrasting with quantum encryption that leverages quantum mechanics for enhanced security against quantum-computing attacks.
Key Differences Between Quantum and Symmetric Encryption
Quantum encryption leverages quantum key distribution (QKD) to ensure unbreakable security based on the principles of quantum mechanics, while symmetric encryption relies on a single shared secret key for both encryption and decryption processes. Quantum encryption provides inherent protection against eavesdropping through the detection of quantum state disturbances, whereas symmetric encryption's security depends heavily on key management and computational complexity. The primary distinction lies in quantum encryption's ability to detect interception attempts, making it more secure against future quantum computing attacks compared to traditional symmetric algorithms like AES.
Security Strength: Quantum Encryption vs Symmetric Encryption
Quantum encryption leverages principles of quantum mechanics, such as quantum key distribution (QKD), to detect eavesdropping and provide theoretically unbreakable security against adversaries with unlimited computational power. Symmetric encryption relies on secret keys and computational hardness assumptions, offering strong security but is potentially vulnerable to future advances in quantum computing that can solve underlying mathematical problems more efficiently. The security strength of quantum encryption surpasses symmetric encryption by ensuring key exchange integrity through quantum states, making it resilient to both classical and quantum attacks.
Performance and Speed Comparisons
Quantum encryption leverages quantum key distribution (QKD) to provide theoretically unbreakable security but currently faces limitations in speed and scalability due to hardware complexity and transmission distances. Symmetric encryption algorithms like AES deliver high-speed data processing and low latency, making them ideal for real-time applications despite relying on classical key management. Performance benchmarks indicate that symmetric encryption outperforms quantum encryption in raw throughput, while quantum methods excel in security for critical key exchange scenarios.
Vulnerabilities to Quantum Attacks
Quantum encryption leverages principles of quantum mechanics to secure communication, making it inherently resistant to interception and eavesdropping by quantum computers. Symmetric encryption, while currently strong, faces potential vulnerabilities as quantum algorithms like Grover's algorithm can reduce their effective security by significantly speeding up key searches. Future-proof cryptographic systems increasingly favor quantum-resistant methods to safeguard data against emerging quantum attacks.
Future-Proofing Data: Is Quantum Encryption Essential?
Quantum encryption leverages the principles of quantum mechanics to secure data, making it theoretically impervious to attacks from classical and quantum computers, unlike symmetric encryption which relies on mathematical complexity vulnerable to future quantum attacks. As quantum computing advances, symmetric encryption algorithms like AES may become obsolete, increasing the urgency for quantum encryption to future-proof sensitive communications. Organizations aiming to protect data integrity against emerging quantum threats must evaluate quantum encryption's potential to provide long-term security beyond the capabilities of traditional symmetric methods.
Practical Applications in Today’s Digital Landscape
Quantum encryption leverages quantum key distribution (QKD) to provide theoretically unbreakable security, making it ideal for securing highly sensitive communications in government and financial sectors. Symmetric encryption, such as AES, remains the backbone of everyday digital security due to its efficiency and speed, widely used in securing data at rest and in transit across most commercial and consumer applications. The integration of quantum encryption with existing symmetric methods is increasingly explored to enhance cryptographic resilience in cloud computing and IoT environments.
Implementation Challenges and Scalability
Quantum encryption faces significant implementation challenges such as the requirement for sophisticated quantum hardware and sensitivity to environmental noise, limiting its current scalability. Symmetric encryption benefits from mature, widely-deployed infrastructure and efficient algorithms but struggles with key distribution and management at large scales. Scalability in quantum encryption depends on advances in quantum repeaters and error correction, whereas symmetric encryption scalability hinges on secure key exchange protocols and computational resource availability.
The Road Ahead: Evolving Encryption Standards
Quantum encryption leverages principles of quantum mechanics to provide theoretically unbreakable security, addressing vulnerabilities inherent in symmetric encryption algorithms reliant on shared secret keys. As quantum computing advances, traditional symmetric encryption faces increasing risks from quantum attacks, prompting research into quantum-resistant algorithms and hybrid cryptographic protocols. The road ahead involves integrating quantum encryption with classical methods to establish evolving encryption standards that ensure data protection in the era of quantum supremacy.
Quantum encryption vs Symmetric encryption Infographic
 difterm.com
difterm.com