Quantum key distribution leverages the principles of quantum mechanics to enable theoretically unbreakable encryption by ensuring any eavesdropping attempt disrupts the quantum states, alerting communicating parties. Classical encryption relies on mathematical algorithms and computational hardness assumptions, which can be vulnerable to advances in computing power and algorithms. The intrinsic security of quantum key distribution offers a promising future for securing sensitive communications against threats from quantum computing.
Table of Comparison
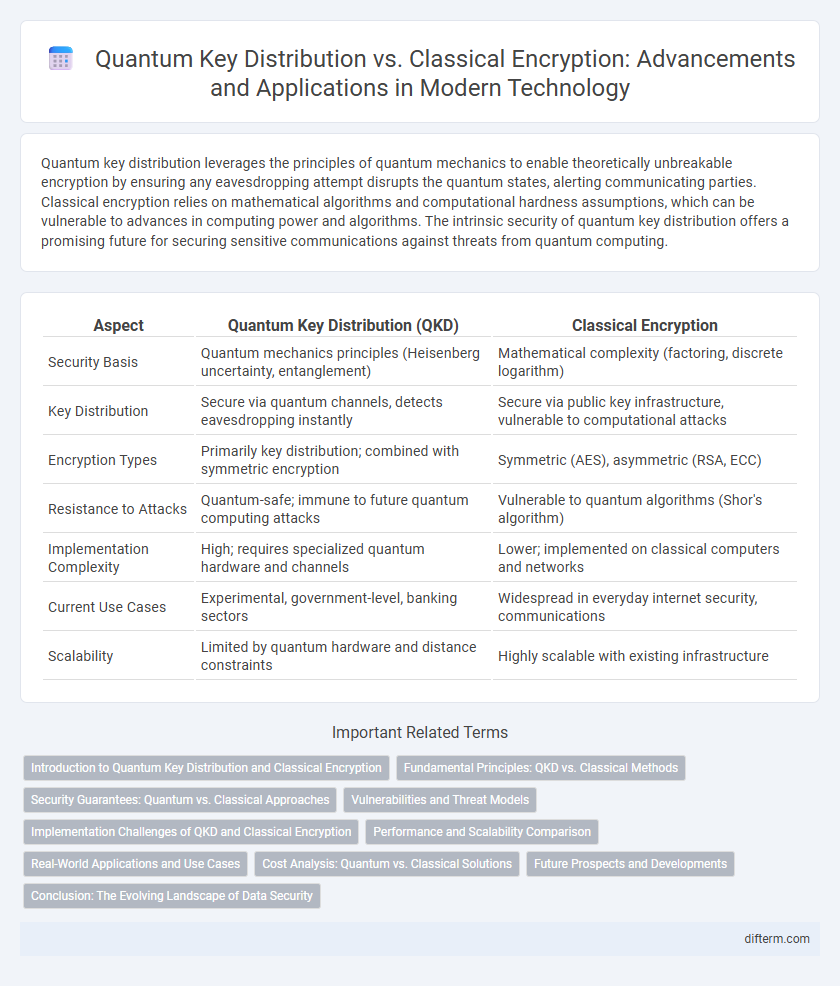
| Aspect | Quantum Key Distribution (QKD) | Classical Encryption |
|---|---|---|
| Security Basis | Quantum mechanics principles (Heisenberg uncertainty, entanglement) | Mathematical complexity (factoring, discrete logarithm) |
| Key Distribution | Secure via quantum channels, detects eavesdropping instantly | Secure via public key infrastructure, vulnerable to computational attacks |
| Encryption Types | Primarily key distribution; combined with symmetric encryption | Symmetric (AES), asymmetric (RSA, ECC) |
| Resistance to Attacks | Quantum-safe; immune to future quantum computing attacks | Vulnerable to quantum algorithms (Shor's algorithm) |
| Implementation Complexity | High; requires specialized quantum hardware and channels | Lower; implemented on classical computers and networks |
| Current Use Cases | Experimental, government-level, banking sectors | Widespread in everyday internet security, communications |
| Scalability | Limited by quantum hardware and distance constraints | Highly scalable with existing infrastructure |
Introduction to Quantum Key Distribution and Classical Encryption
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to securely exchange cryptographic keys, enabling theoretically unbreakable encryption by detecting any eavesdropping attempts. Classical encryption methods, such as RSA and AES, rely on complex mathematical algorithms and computational hardness assumptions, which are vulnerable to advances in computing power, particularly quantum computing. QKD provides enhanced security by utilizing quantum states for key exchange, contrasting with classical encryption's dependence on algorithmic complexity.
Fundamental Principles: QKD vs. Classical Methods
Quantum key distribution (QKD) leverages the principles of quantum mechanics, such as photon polarization and quantum superposition, to enable secure key exchange that is provably immune to eavesdropping. Classical encryption relies on mathematical algorithms and computational hardness assumptions, like factoring large primes or discrete logarithms, which can be vulnerable to advances in computing power. QKD's security is based on physical laws rather than computational complexity, making it resilient against attacks from both classical and quantum computers.
Security Guarantees: Quantum vs. Classical Approaches
Quantum key distribution (QKD) offers theoretically unbreakable security based on the principles of quantum mechanics, ensuring any eavesdropping attempt disturbs the quantum states and is immediately detectable. Classical encryption relies on computational hardness assumptions, making it vulnerable to advances in algorithms and quantum computing attacks. As a result, QKD provides superior security guarantees by physically preventing key interception, while classical methods depend on the current limits of computational power.
Vulnerabilities and Threat Models
Quantum key distribution (QKD) offers enhanced security by leveraging principles of quantum mechanics to detect eavesdropping, eliminating risks that classical encryption faces from brute force attacks and computational advances. Classical encryption relies on mathematical complexity, making it vulnerable to advances in quantum computing that can efficiently solve problems like factoring large primes. Threat models for QKD assume an adversary cannot clone quantum states without detection, whereas classical methods require assumptions about computational limits and key management practices.
Implementation Challenges of QKD and Classical Encryption
Quantum key distribution (QKD) faces implementation challenges including the need for specialized hardware such as photon detectors, susceptibility to environmental noise, and limitations in transmission distance over optical fibers. Classical encryption relies heavily on computational hardness assumptions but struggles with vulnerabilities posed by advances in quantum computing and the increasing complexity of key management. Both technologies require ongoing developments in error correction, secure key exchange protocols, and integration with existing communication infrastructures to ensure robust security.
Performance and Scalability Comparison
Quantum key distribution (QKD) offers unmatched security by leveraging quantum mechanics principles but faces challenges in performance due to limited transmission distances and slower key generation rates compared to classical encryption methods. Classical encryption algorithms like AES excel in scalability and speed, supporting high-throughput data encryption across global networks with minimal latency. While QKD's performance is constrained by current quantum hardware limitations, ongoing advancements aim to enhance its scalability for integration into existing communication infrastructures.
Real-World Applications and Use Cases
Quantum key distribution (QKD) enhances security for critical communications in finance, defense, and healthcare by enabling unbreakable encryption through quantum mechanics principles. Classical encryption methods, while widely adopted, face vulnerabilities from advancing computational power and quantum computing threats, making QKD essential for future-proof data protection. Real-world implementations of QKD include secure satellite communications, government networks, and secure data transmission in cloud computing environments.
Cost Analysis: Quantum vs. Classical Solutions
Quantum key distribution (QKD) demands significant initial investment in specialized hardware such as photon sources and single-photon detectors, making upfront costs considerably higher than classical encryption systems that rely on widely available computational resources. Operational costs for QKD remain elevated due to the need for maintaining quantum channels and error correction protocols, while classical encryption benefits from mature infrastructure and lower energy consumption. Despite higher expenses, QKD offers unparalleled security against quantum attacks, potentially reducing long-term risks and costs associated with data breaches in comparison to classical encryption methods vulnerable to evolving computational power.
Future Prospects and Developments
Quantum key distribution (QKD) represents a transformative advancement in secure communication by leveraging the principles of quantum mechanics to provide theoretically unbreakable encryption keys. Unlike classical encryption, which relies on mathematical complexity and is vulnerable to future quantum computing attacks, QKD ensures security through the fundamental laws of physics, making it a cornerstone technology for next-generation cybersecurity. Ongoing developments in quantum repeaters, satellite-based QKD networks, and integration with existing communication infrastructure signal a promising future where QKD could become the standard for global secure data transmission.
Conclusion: The Evolving Landscape of Data Security
Quantum key distribution (QKD) offers unprecedented security by leveraging the principles of quantum mechanics, making eavesdropping detectable and theoretically unbreakable. Classical encryption methods, while currently widespread and efficient, face increasing threats from advances in computational power and algorithmic breakthroughs. The future of data security will likely involve hybrid systems integrating QKD to enhance encryption protocols and protect sensitive information against emerging cyber threats.
quantum key distribution vs classical encryption Infographic
 difterm.com
difterm.com