Public key cryptography uses a pair of keys: a public key shared openly for encrypting data and a private key kept secret for decrypting it, ensuring secure communication. The public key allows anyone to send encrypted messages, but only the holder of the private key can access the original information. This method underpins secure transactions, digital signatures, and authentication protocols in modern technology.
Table of Comparison
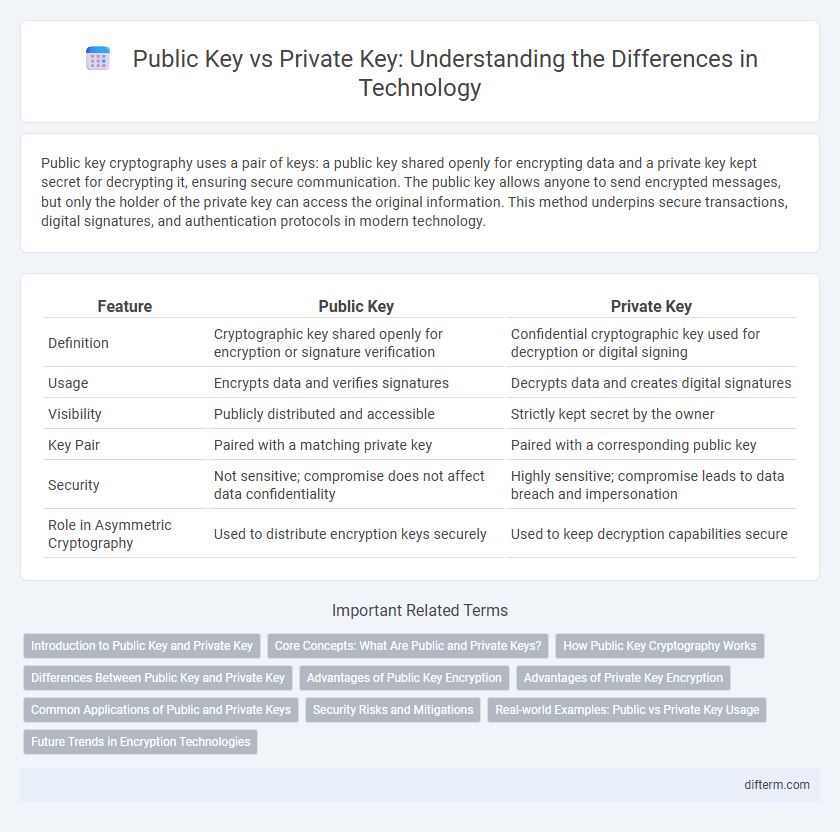
| Feature | Public Key | Private Key |
|---|---|---|
| Definition | Cryptographic key shared openly for encryption or signature verification | Confidential cryptographic key used for decryption or digital signing |
| Usage | Encrypts data and verifies signatures | Decrypts data and creates digital signatures |
| Visibility | Publicly distributed and accessible | Strictly kept secret by the owner |
| Key Pair | Paired with a matching private key | Paired with a corresponding public key |
| Security | Not sensitive; compromise does not affect data confidentiality | Highly sensitive; compromise leads to data breach and impersonation |
| Role in Asymmetric Cryptography | Used to distribute encryption keys securely | Used to keep decryption capabilities secure |
Introduction to Public Key and Private Key
Public key and private key are fundamental components of asymmetric cryptography, enabling secure communication over unsecured networks. The public key is openly shared and used to encrypt data, while the private key remains confidential and is used to decrypt the received information. This cryptographic system ensures data integrity and authentication, essential in digital signatures and secure online transactions.
Core Concepts: What Are Public and Private Keys?
Public keys and private keys are fundamental components of asymmetric encryption, where the public key encrypts data and the private key decrypts it. The public key is openly shared to enable secure communication, while the private key remains confidential to ensure data integrity and authentication. This cryptographic pair enables secure transactions, digital signatures, and confidential information exchange in technology systems.
How Public Key Cryptography Works
Public key cryptography operates using a pair of mathematically related keys: a public key, which is openly shared, and a private key, kept secret by the owner. Data encrypted with the public key can only be decrypted by the corresponding private key, ensuring secure communication and authentication. This asymmetric encryption method enables secure data exchange without requiring the sharing of private keys, enhancing confidentiality and integrity in digital communications.
Differences Between Public Key and Private Key
Public key cryptography involves a pair of keys: the public key, which is shared openly, and the private key, which remains confidential to the owner. The public key encrypts data, while the private key decrypts it, ensuring secure communication and authentication. Differences between these keys include their roles in encryption/decryption, key distribution methods, and their usage in digital signatures versus data confidentiality.
Advantages of Public Key Encryption
Public key encryption enhances security by using two distinct keys: a public key for encryption and a private key for decryption, eliminating the need to share sensitive private keys. It enables secure communication over unsecured networks and facilitates digital signatures for authentication and non-repudiation. The widespread adoption in protocols such as SSL/TLS and PGP highlights its critical role in safeguarding internet transactions and confidential data.
Advantages of Private Key Encryption
Private key encryption offers significant advantages by enabling faster data processing speeds due to its symmetric nature, where the same key is used for both encryption and decryption. This method enhances efficiency in securing large volumes of data with minimal computational overhead, making it ideal for real-time communication. Additionally, private key encryption provides strong confidentiality as the key remains solely with authorized parties, reducing the risk of interception during key exchange.
Common Applications of Public and Private Keys
Public keys are extensively used in secure communications such as SSL/TLS protocols to enable encrypted data exchange between web browsers and servers. Private keys are essential for digital signatures and authentication processes, ensuring data integrity and verifying the identity of the sender. Both keys form the backbone of asymmetric cryptography in applications like email encryption, cryptocurrency transactions, and secure access to sensitive data.
Security Risks and Mitigations
Public key cryptography involves using paired keys where the public key encrypts data and the private key decrypts it, minimizing exposure of sensitive information. Security risks include private key theft, which can lead to unauthorized access and data breaches, mitigated by hardware security modules (HSMs) and multi-factor authentication (MFA). Regular key rotation, strong encryption algorithms like RSA or ECC, and secure key storage practices are essential to prevent compromise and maintain data integrity.
Real-world Examples: Public vs Private Key Usage
Public keys are commonly used in SSL/TLS certificates to enable secure web browsing by encrypting data sent from a user's browser, ensuring confidentiality without revealing private keys. Private keys, stored securely by individuals or organizations, authenticate identity and decrypt data, such as in Bitcoin wallets where private keys allow users to authorize cryptocurrency transactions. Public key infrastructure (PKI) systems utilize pairs of public and private keys for email encryption, digital signatures, and secure communications in corporate environments, highlighting their distinct but complementary roles in cybersecurity.
Future Trends in Encryption Technologies
Public key and private key encryption systems are evolving with advancements in quantum-resistant algorithms designed to safeguard data against emerging threats from quantum computing. The integration of machine learning models enhances key generation, enabling dynamic encryption methods that adapt to potential vulnerabilities in real-time. Future trends emphasize decentralized key management frameworks to improve security and scalability across distributed networks and IoT devices.
Public key vs Private key Infographic
 difterm.com
difterm.com