Multi-factor authentication (MFA) offers stronger security than two-factor authentication (2FA) by requiring multiple verification methods from different categories, such as biometrics, hardware tokens, and passwords. While 2FA typically involves just two factors, often a password plus a text code, MFA expands protection by incorporating additional layers, significantly reducing the risk of unauthorized access. Organizations favor MFA to safeguard sensitive data and enhance overall cybersecurity resilience.
Table of Comparison
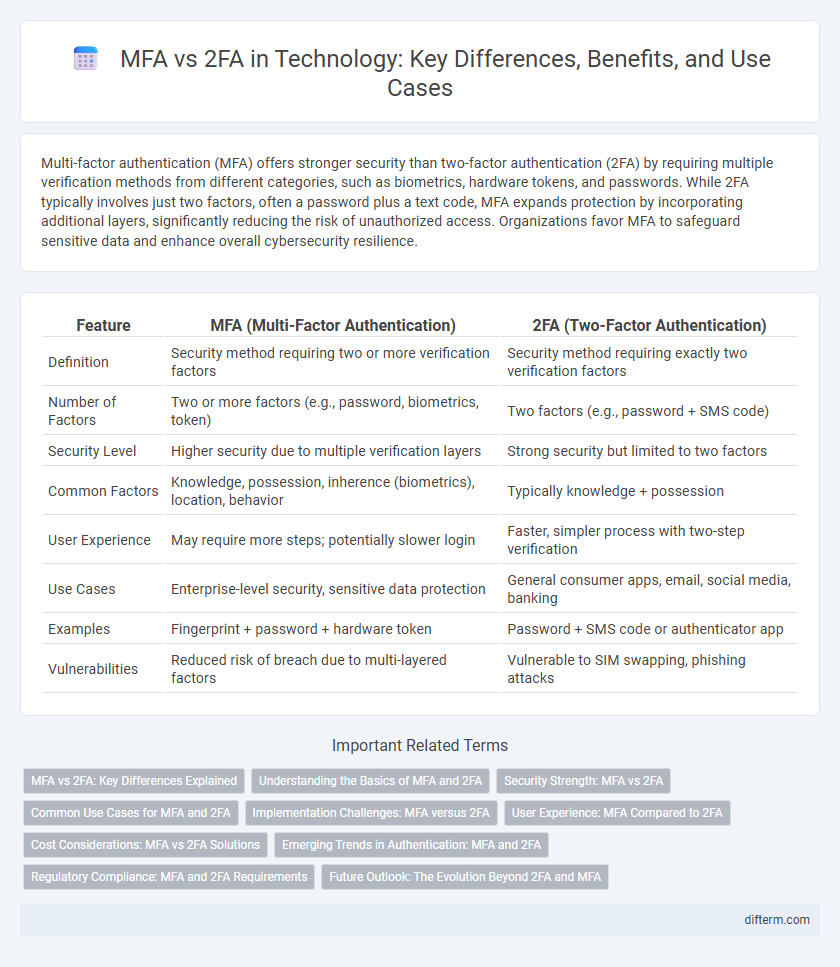
| Feature | MFA (Multi-Factor Authentication) | 2FA (Two-Factor Authentication) |
|---|---|---|
| Definition | Security method requiring two or more verification factors | Security method requiring exactly two verification factors |
| Number of Factors | Two or more factors (e.g., password, biometrics, token) | Two factors (e.g., password + SMS code) |
| Security Level | Higher security due to multiple verification layers | Strong security but limited to two factors |
| Common Factors | Knowledge, possession, inherence (biometrics), location, behavior | Typically knowledge + possession |
| User Experience | May require more steps; potentially slower login | Faster, simpler process with two-step verification |
| Use Cases | Enterprise-level security, sensitive data protection | General consumer apps, email, social media, banking |
| Examples | Fingerprint + password + hardware token | Password + SMS code or authenticator app |
| Vulnerabilities | Reduced risk of breach due to multi-layered factors | Vulnerable to SIM swapping, phishing attacks |
MFA vs 2FA: Key Differences Explained
Multi-Factor Authentication (MFA) enhances security by requiring two or more verification methods, such as biometrics, hardware tokens, or one-time passwords, compared to Two-Factor Authentication (2FA), which strictly involves two distinct factors. MFA provides a broader range of authentication options, reducing the risk associated with compromised credentials, while 2FA typically combines something you know (password) and something you have (phone or token). The key difference lies in MFA's ability to incorporate multiple layers of defense, offering stronger protection for sensitive systems and data against unauthorized access.
Understanding the Basics of MFA and 2FA
Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) are security protocols designed to verify user identity by requiring multiple forms of verification. 2FA is a subset of MFA, typically involving two distinct factors such as a password and a one-time code sent to a mobile device, while MFA can include two or more factors like biometrics, security tokens, or location data. Understanding these basics highlights how MFA provides a higher security level by incorporating additional authentication layers beyond the two factors used in 2FA.
Security Strength: MFA vs 2FA
Multi-Factor Authentication (MFA) offers enhanced security strength compared to Two-Factor Authentication (2FA) by requiring users to verify identity through multiple independent factors such as biometrics, hardware tokens, and one-time passwords. 2FA typically involves only two verification methods, often combining a password with a secondary code, which while effective, presents a lower barrier to sophisticated cyber-attacks than MFA's layered approach. Organizations adopting MFA significantly reduce the risk of unauthorized access and data breaches owing to its comprehensive authentication mechanisms.
Common Use Cases for MFA and 2FA
Multi-Factor Authentication (MFA) is widely used in enterprises for securing access to sensitive data, cloud services, and corporate networks by requiring multiple verification methods such as biometrics, security tokens, and passwords. Two-Factor Authentication (2FA) is commonly applied in consumer applications like email, social media, and online banking, typically combining a password with a text message or app-based verification code. MFA offers a broader security layer by incorporating various factors beyond the two-step process typical of 2FA, enhancing protection in high-risk environments.
Implementation Challenges: MFA versus 2FA
Multi-factor authentication (MFA) implementation often faces challenges related to complexity and user experience compared to two-factor authentication (2FA), as MFA requires integrating multiple authentication factors beyond just two. Organizations encounter higher costs and longer deployment times due to the need for advanced infrastructure and comprehensive user training. Ensuring compatibility across diverse devices and applications further complicates MFA rollout, whereas 2FA adoption tends to be more straightforward with fewer integration issues.
User Experience: MFA Compared to 2FA
Multi-Factor Authentication (MFA) enhances user experience by offering flexibility through multiple verification methods such as biometrics, hardware tokens, and app-based codes, beyond the traditional SMS or email codes used in Two-Factor Authentication (2FA). MFA reduces friction by adapting to user preferences and device capabilities, improving security without significantly increasing login time or complexity. Compared to 2FA, MFA provides a more seamless and secure authentication process that better aligns with modern user demands for convenience and protection.
Cost Considerations: MFA vs 2FA Solutions
Multi-Factor Authentication (MFA) solutions generally incur higher implementation and maintenance costs compared to Two-Factor Authentication (2FA) due to the integration of multiple verification methods such as biometrics, hardware tokens, and behavioral analysis. While 2FA primarily relies on two verification factors like SMS codes or authenticator apps, MFA's advanced security layers require more robust infrastructure and ongoing management expenses, impacting budget allocations. Organizations must weigh the higher upfront and operational costs of MFA against its enhanced security benefits and potential reduction in breach-related financial losses.
Emerging Trends in Authentication: MFA and 2FA
Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) enhance security by requiring multiple verification methods, with MFA typically involving three or more factors such as biometrics, tokens, and passwords. Emerging trends in authentication emphasize adaptive and risk-based MFA systems that dynamically adjust verification requirements based on user behavior and threat levels. Advancements in biometric technologies, behavioral analytics, and AI-driven fraud detection are shaping the future of robust, user-friendly authentication frameworks.
Regulatory Compliance: MFA and 2FA Requirements
Multifactor Authentication (MFA) and Two-Factor Authentication (2FA) are critical components in meeting regulatory compliance standards such as GDPR, HIPAA, and PCI DSS. MFA, requiring multiple verification methods from different categories (knowledge, possession, inherence), offers stronger protection compared to 2FA, which typically involves only two layers of the same or different categories. Regulatory frameworks increasingly mandate MFA to enhance security protocols and reduce the risk of unauthorized access, making it essential for organizations to implement comprehensive authentication strategies that align with compliance requirements.
Future Outlook: The Evolution Beyond 2FA and MFA
Future security frameworks are evolving beyond traditional two-factor authentication (2FA) and multi-factor authentication (MFA) by integrating biometric verification, behavioral analytics, and artificial intelligence for adaptive risk assessment. Passwordless authentication methods using hardware tokens and decentralized identity models are gaining traction, offering enhanced protection against emerging cyber threats. These advancements signify a shift towards more seamless, context-aware security paradigms that balance user experience with stronger fraud prevention.
MFA vs 2FA Infographic
 difterm.com
difterm.com